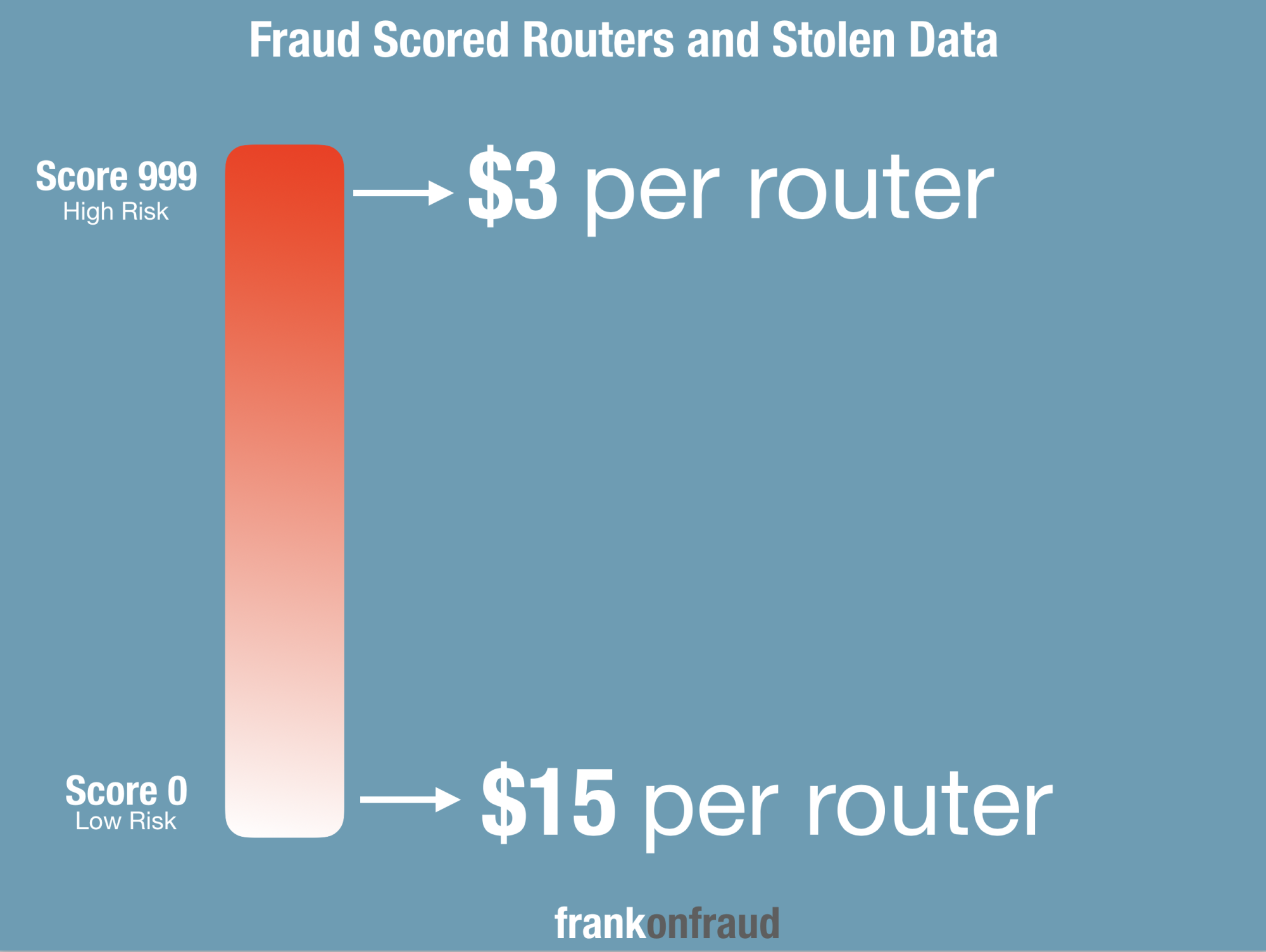
Your yahoo account credentials from 1999 may sell for 10 cents on the dark web, but your Netflix username and password could fetch $2 or more. Access to your router, however, could run as high as $15 if it’s considered low risk by hackers.
It’s all because hackers are using the same types of fraud scoring techniques banks have used for decades to understand which account is riskier.
The hackers are now using fraud scoring to determine how likely it is that a bank or merchant will find the information risky.
If a bank identifies it as risky, it is much more likely to get shut down immediately. But if it is a low fraud score, it is much more likely that a fraudster can use the information for a longer period undetected.
Those fraud scores help fraudsters determine which credentials are likely to result in the greatest return on investment. If the router scores low, they charge a higher price. If the router scores high, they can only charge a lower price.
The FBI Was Tipped Off On Novel Use of Fraud Scoring This Week
This week, the FBI was tipped off about a cybercriminal operation where a hacker managed not only to breach 130,000 Asus routers but they were also scoring them to determine how useful they might be for fraudsters.
The hackers were selling access to these routers to fraudsters so that they could run their traffic through them while committing fraud.
Forbes reports that the hacker is selling this combination of hacked routers and fraud scores in packages via Qiwi, a Russian alternative to PayPal.
They range in price, from around $3 to $15. For instance, access to a router with a zero risk score costs around $15
They Also Enriched The Data In Other Ways
To increase the value of the data, the hacker also juiced the data by combining it with other breached data.
The hacker is also selling stolen credit card data and access to a database containing information on 500,000 consumers, including their name, address, social security number and date of birth.
Why This is Valuable to The Fraudsters
This is valuable to fraudsters because they can use the combination of stolen PII and low-risk routers to essentially better disguise their illicit activity to make it look normal.
So for example, if a fraudster buys stolen credit card information from an individual in Nebraska and then uses a low-risk router in Nebraska nearby, their activity is very likely to look very legitimate. This approach is helping fraudsters avoid the Geolocation rules that banks and merchants use to identify customers that are legitimate from those that are fraudsters.
According to Forbes, Researchers believe that fraudsters will select low-scoring fraud risk routers in a victim’s location and either get direct access to the devices or route their traffic through them via a VPN before they buy items on stolen credit cards. Alternatively, the fraudsters could register entirely new credit cards with stolen identities, again in the right region and on a clean-looking IP address.
And they are doing all of this with the help of the same type of fraud scoring technology that banks may be using to identify it in the first place increasing their odds of success.
Read the Whole White Ops Report Here
If you want to read the complete report by WhiteOps, you can check it out here – DoppleGangers Delight: How One Person is Exploiting Your WiFi Router.
In the report they detail how the routers were hacked but also provide an indication of some of the quality checks and enhancements that the hackers did to the data including:
Some of the quality checks that can account for high-risk scores include:
- Risk Score: when given an IP address, the system will return a probabilistic value of how likely the IP address is a “bad” IP address.
- Fraud Score: this is the overall fraud score of the user based on the IP address, user agent, language, and any other optionally passed variables.
- Blacklists: this is a reference of whether the IP address has been blacklisted anywhere before.
- Geolocation: where is this IP address located?
The White Ops Threat Intelligence discovered a database with more than 500K U.S. victims’ PII including name, full address, social security number, and date of birth. The fraudster likely obtained this by either stealing it or acquiring it from a previous data breach.
This is a fascinating trend in data breaches that show where they are likely heading in the future.



