It was my first day at the new job. ?♂️ My manager pointed to a cubicle and said that’s where you’re going to sit.
The desk had a phone and an old computer. ☎️
Tess – my co-worker and very first fraud trainer, dropped a stack of paper ? on my desk and said, “Time to find some fraud!”
What she delivered to me were about 50 paper credit card applications that were mailed to First Deposit Bank (my employer) from applicants all over the United States.
My job? Look for people that put a “dot” at the end of their signature.
A Credit Card Boom Gave Fraudsters A Golden Ticket
The 1980s was the golden age of credit cards, and by the early 1990s, the competition was red hot.
To compete, banks were mailing millions of unsolicited credit card applications to consumers all over the US. Consumers could put in a few pieces of information, sign the application and return it back in the postage-paid envelope provided.
The marketing people and fraud rings loved it. The fraud management people – not much.
All those mailers gave fraudsters a golden ticket and ushered in a new wave of mail theft and one of the first identity theft crises we ever experienced here in the US.

It was right around this time that banks started hiring hundreds of fraud analysts to help stop the wave of fraud that began to hit them
And that was precisely when I got my start.
A Tell-Tale Sign Of Application Fraud Back In 1990
When I asked my fraud mentor/trainer, Tess, how I could spot fraud on the 50+ applications she had dropped on my desk, she replied, “Easy”.
She proceeded to divide the stack of applications into two piles.
She picked up the first application and gave it a quick glance.
She dropped it in the first pile stating, “Not Fraud”. And then she did the same thing 3 more times.
When she got to the 5th application, she paused and looked at it a bit longer.
She squinted a bit, then dropped the application into the second pile and said, “That one’s fraud”. Then she picked up a stamp, pressed it on a red ink pad, and stamped “Unable To Verify” on the application.
I was in awe. How did she do it?
It turns out she was looking for the one tell-tale sign that all fraud rings were using at the time. She was looking for a pronounced dot or period at the end of the signature.
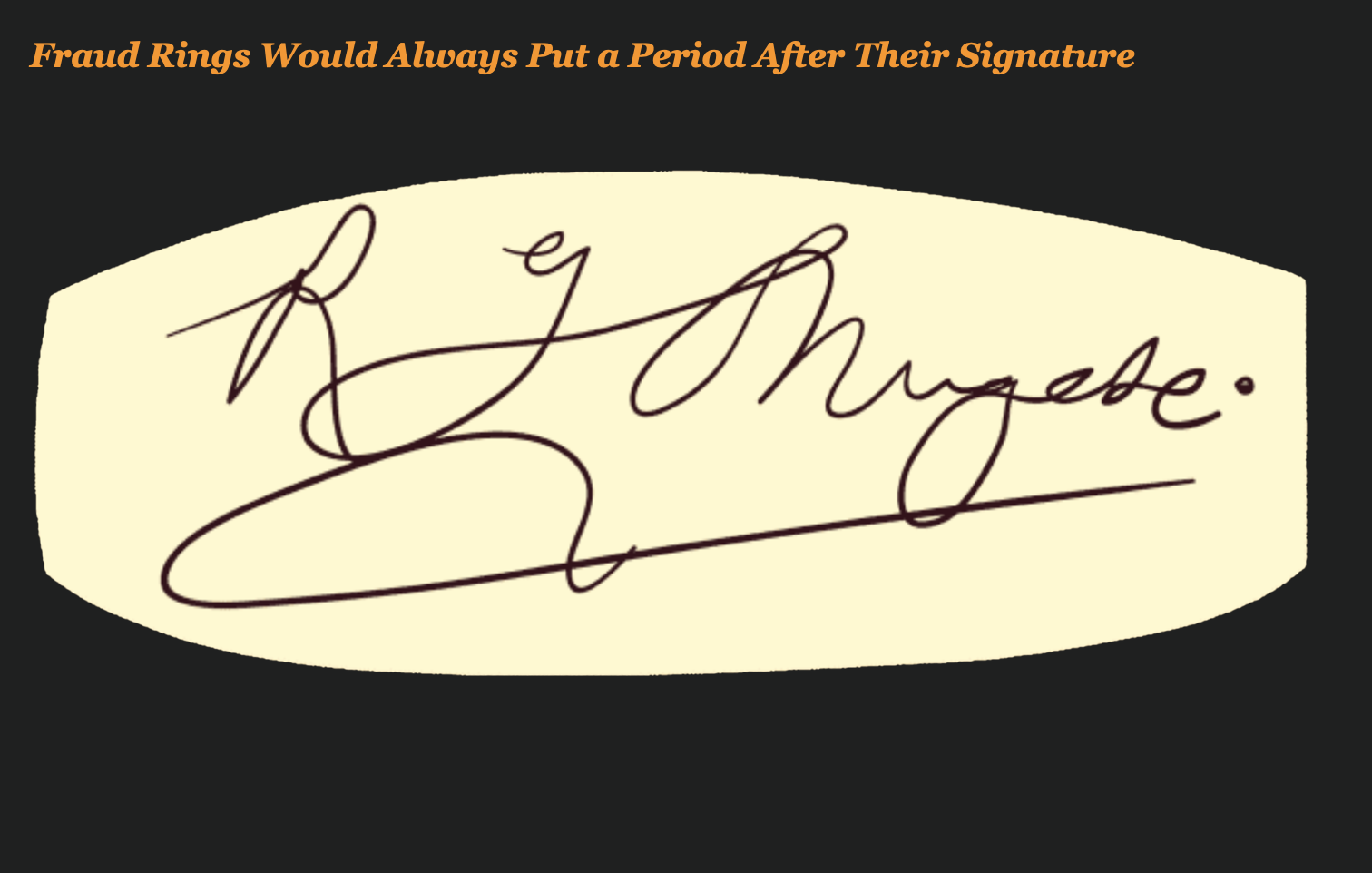
I am not sure why the fraud rings did this but many in the industry suspected that Nigerian fraud rings were behind the mail thefts at the time and that was just how they forged signatures.
Maybe it is because they were filling out hundreds and hundreds of applications a day and they instinctually would put a period at the end of the signature because that signaled that they were done filling it out.
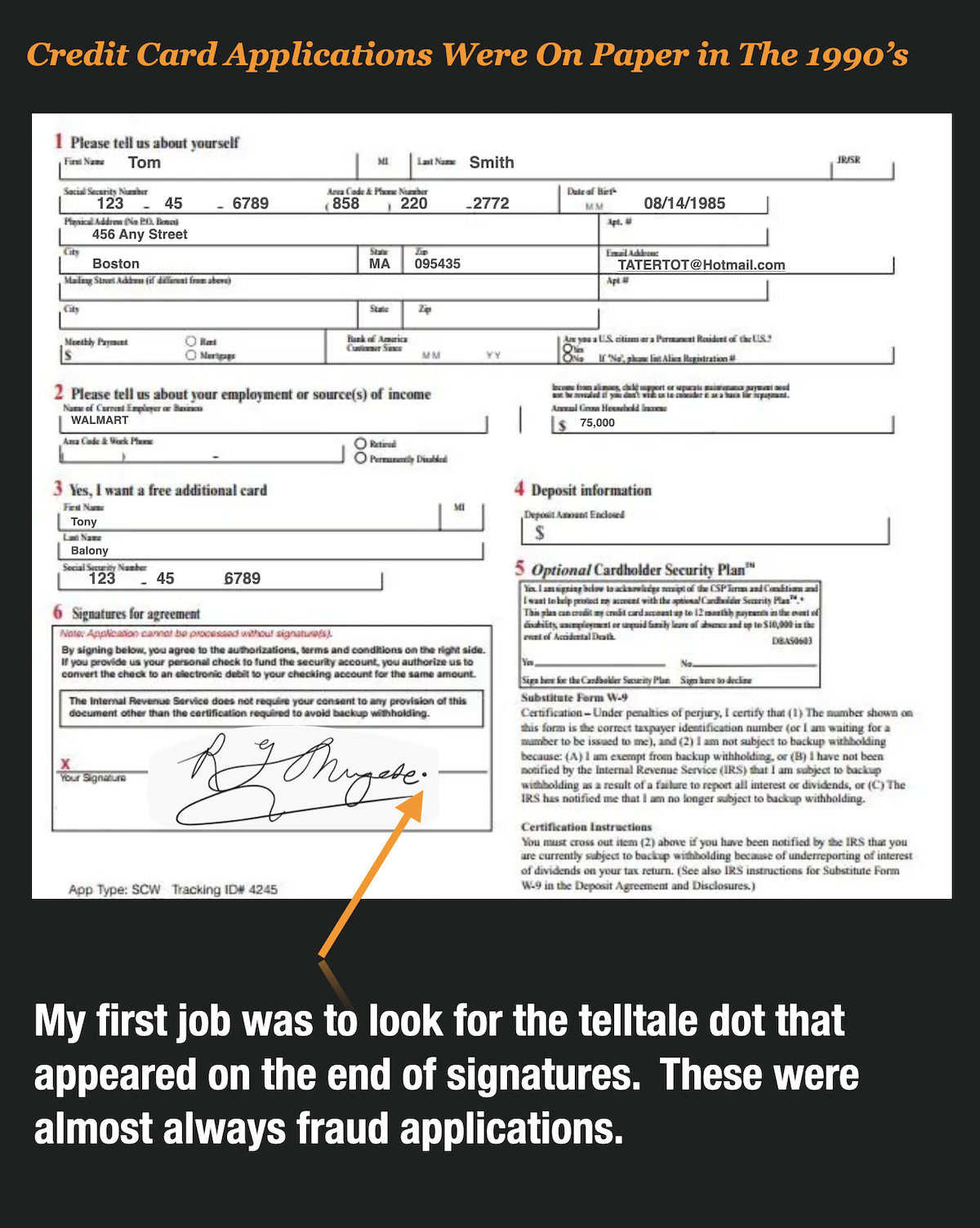
The funny thing about this is, I recently learned that my friend and fellow fraud-fighter Mary Ann Miller started her career doing exactly the same thing as me back in the 1990’s.
Mary Ann worked for First Union at the time, and I worked for First Deposit.
Fraud Tech Has Come A Long Way
Fraud technology certainly has come a long way from those early days of fraud detection. In the 90’s, there wasn’t any identity fraud technology whatsoever.
- There were no bureau alerts
- There were no identity fraud scores
- There were no consortiums or identity networks
- There were no negative files or bad actor databases
The only fraud detection that existed was fraud analyst putting their eyeballs on applications to look for red flags and checking out manually if the information on the application matched to the credit bureau.

Now, identity fraud is a huge business. According to Liminal, thousands of companies are focused on helping resolve identities.
Who would have thought we would have come this far from those lowly days of looking for dotted signatures?
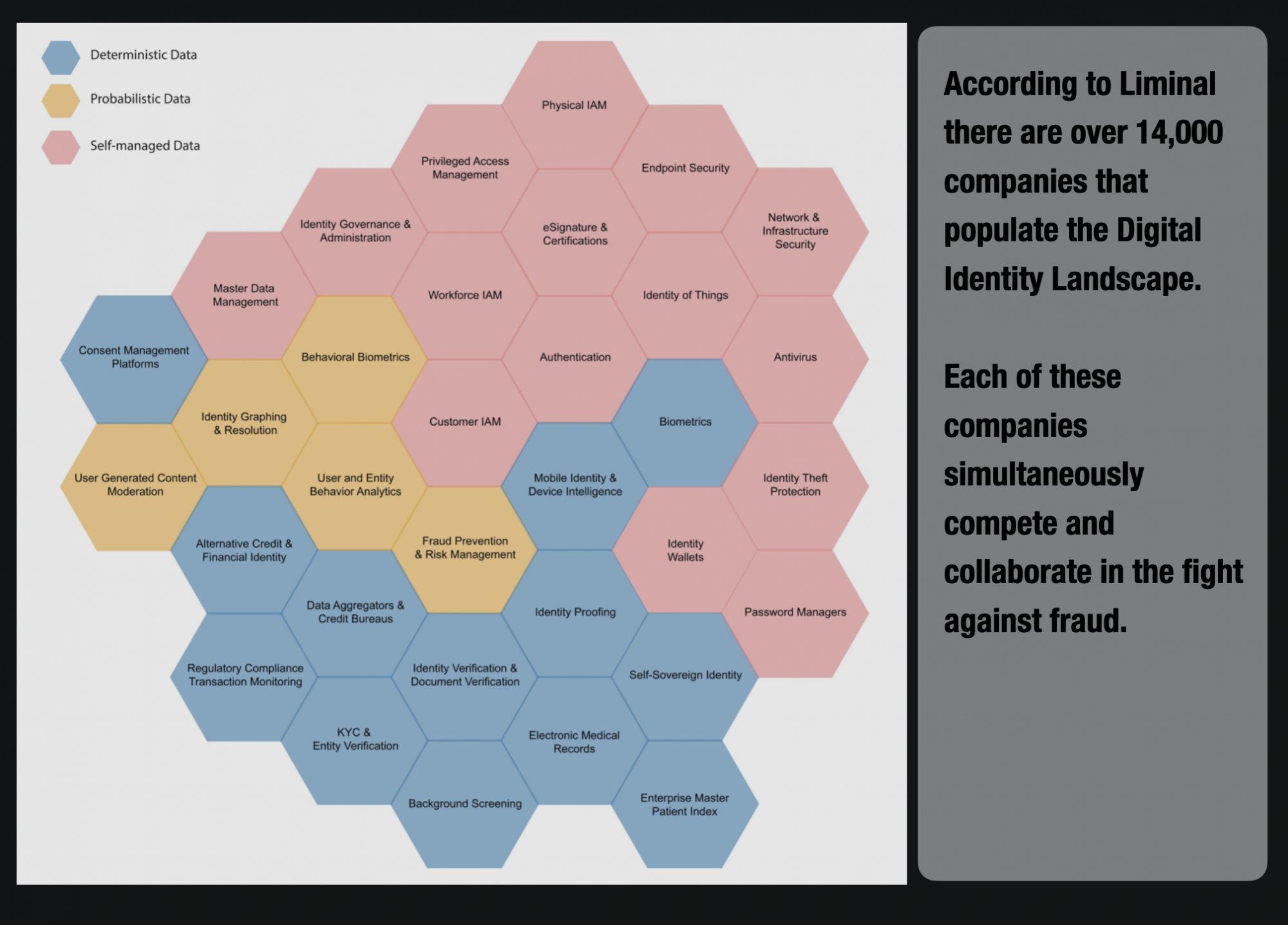
Sure those were great memories but I am glad that technology has evolved.



