The largest DDOS attack in history was launched against a Financial Institution this month and it was stopped. It was stopped so well, that no one even knew it occurred.
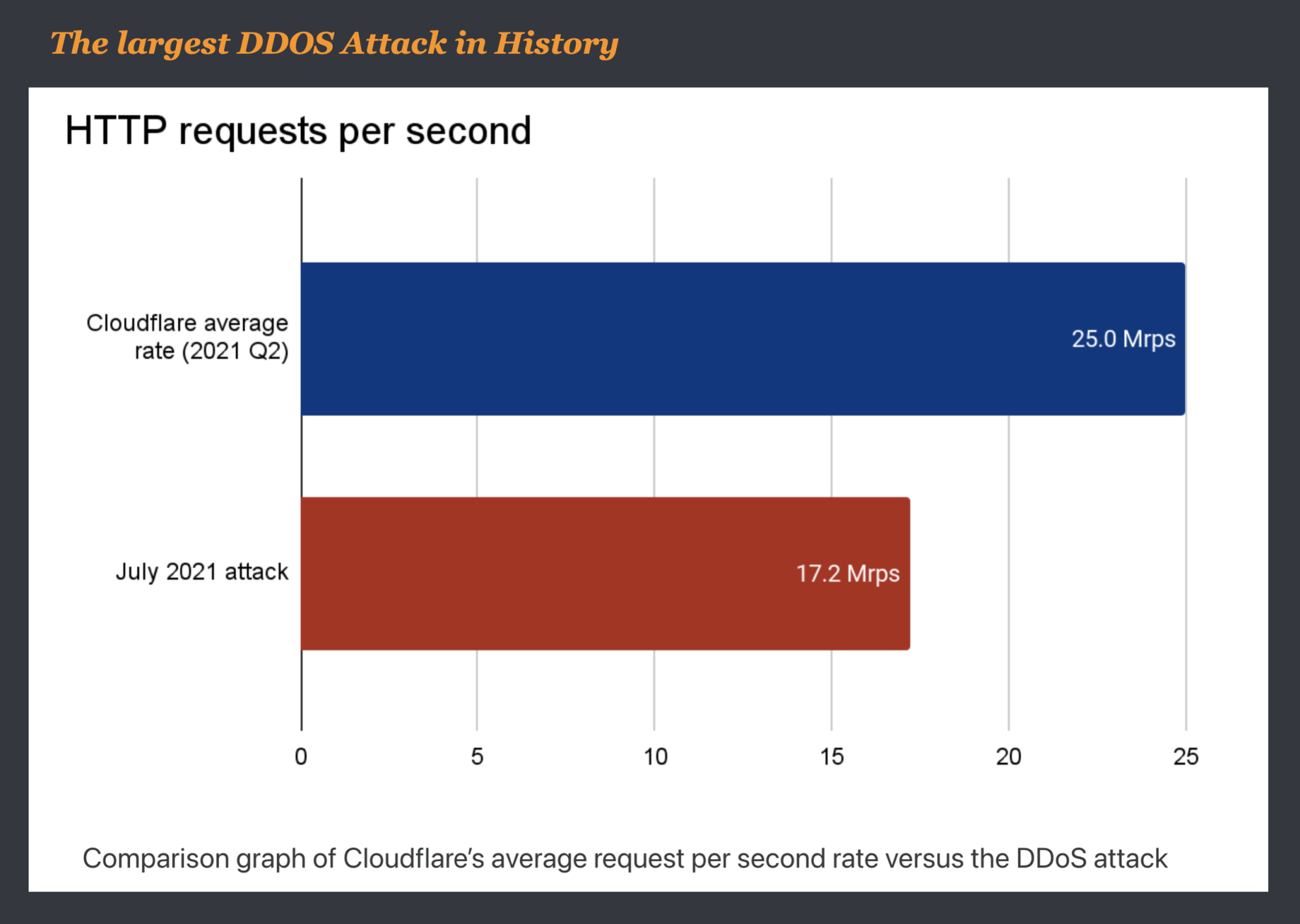
ZDnet .com reported that Cloudflare said it’s system managed to stop the largest reported DDoS attack in July, explaining in a blog post that the attack was 17.2 million requests-per-second, three times larger than any previous one they recorded.
According to a blog post by Omer Yoachimik, CloudFlare serves over 25 million HTTP requests per second on average in 2021 Q2 but this attack nearly doubled the volume per second, which shows the enormity of the attack.
The Attack Was Against a Financial Institution
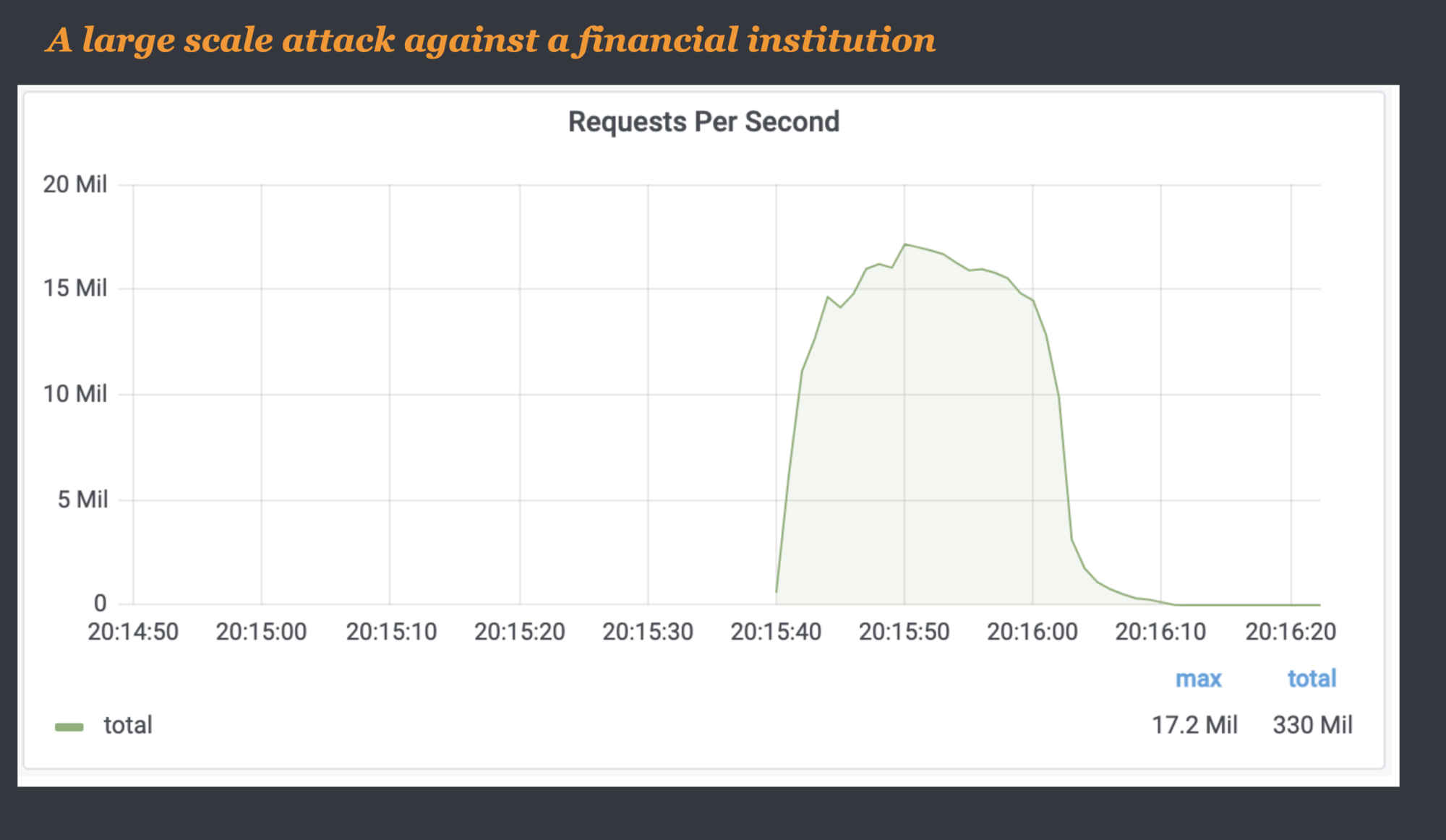
The DDOS attack which was 3 times the size of any other attack in history was launched against a financial institution customer of Cloudflare. The botnet attack delivered over 330 million request within seconds before subsiding.
The Attack Was Thwarted by Cloudflare’s Autonomous Edge
Yoachimik notes that this attack, along with the additional attacks provided in the next sections, were automatically detected and mitigated by Cloudflare’s autonomous edge DDoS protection systems.
Once an attack is detected, Cloudflare systems generate a mitigation rule with a real-time signature that matches the attack patterns. The rule is then propagated to the most optimal location in the tech stack.
The technology is impressive, allowing Cloudflare to mitigate attacks that reach 68% of our average per-second-rate, and higher, without requiring any manual mitigation by Cloudflare personnel, nor causing any performance degradation.
An Army of IOT Devices Across The World
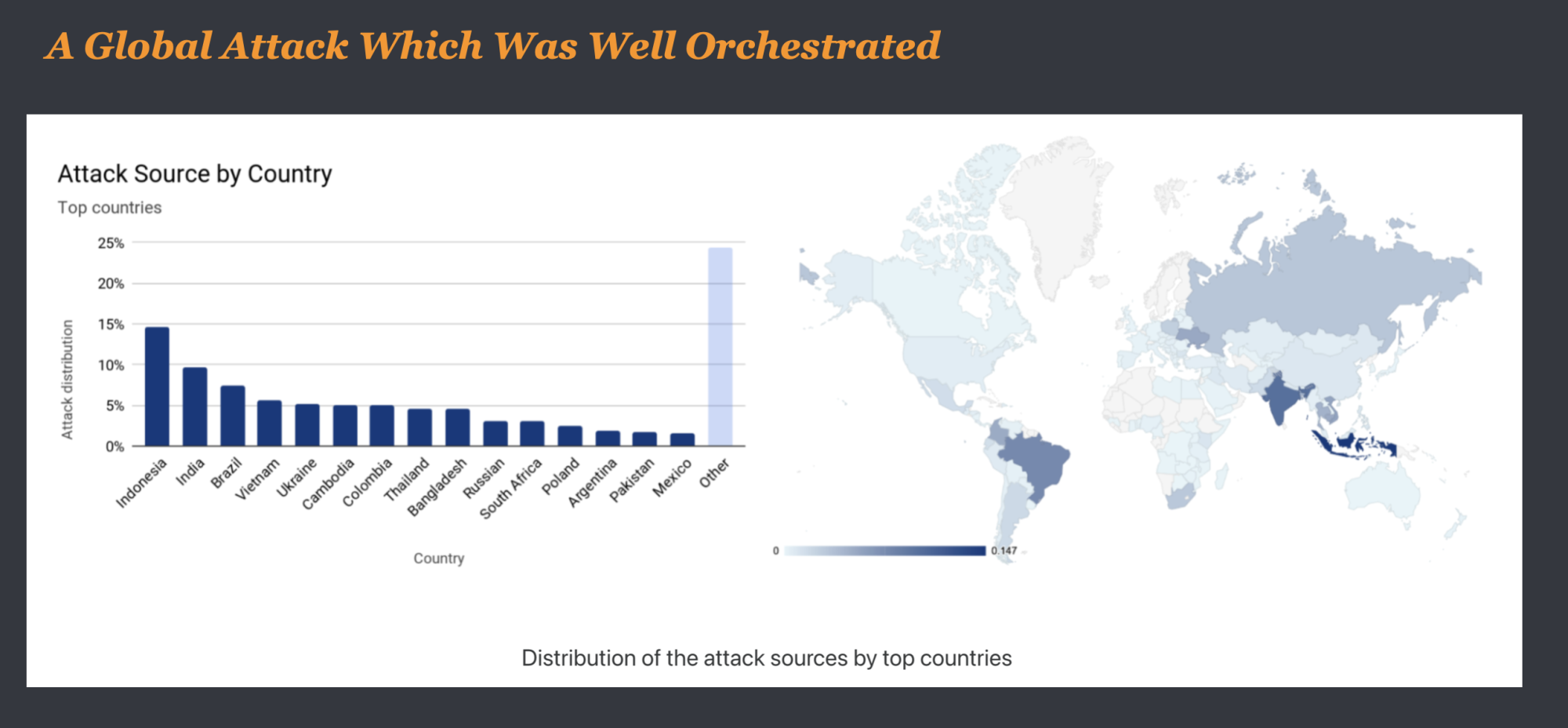
According to Yoachimik‘s blog post, the attack traffic originated from more than 20,000 bots in 125 countries around the world. Based on the bots’ source IP addresses, almost 15% of the attack originated from Indonesia and another 17% from India and Brazil combined. Indicating that there may be many malware-infected devices in those countries.
Yoachimik writes that “These attacks join the increase in Mirari-based DDoS attacks that we’ve observed on our network over the past weeks. In July alone, L3/4 Mirai attacks increased by 88% and L7 attacks by 9%,” Yoachimik said.
Mirai, which means ‘future’ in Japanese, is a codename for malware that was first discovered in 2016 by MalwareMustDie, a non-profit security research workgroup. The malware spreads by infecting Linux-operated devices such as security cameras and routers. It then self-propagates by searching for open Telnet ports 23 and 2323.
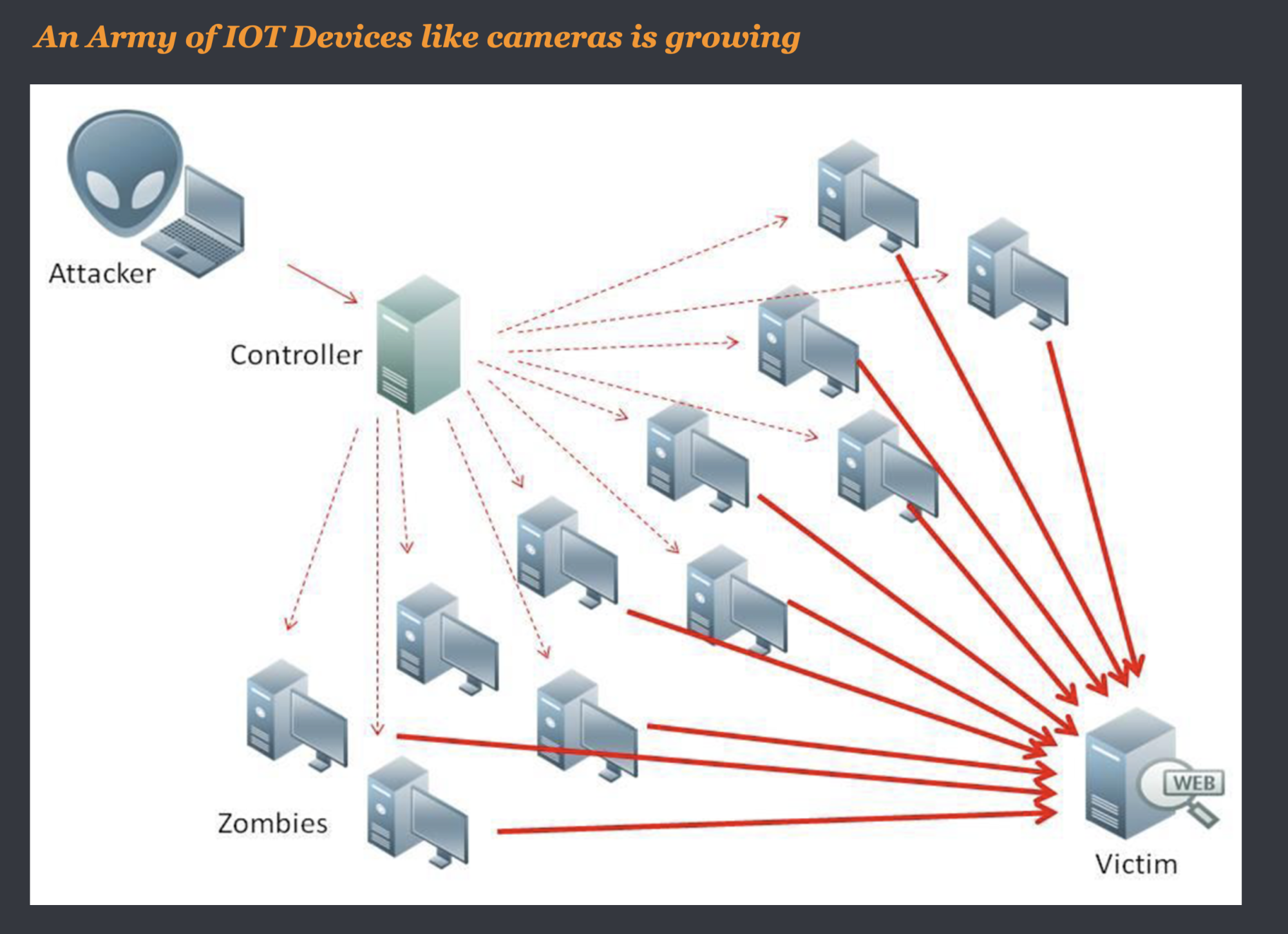
Once found, it then attempts to gain access to vulnerable devices by brute forcing known credentials such as factory default usernames and passwords. Later variants of Mirai also took advantage of zero-day exploits in routers and other devices. Once infected, the devices will monitor a Command & Control (C2) server for instructions on which target to attack.
According to ZDNET this was a well-orchestrated and professional attack. They spoke with an expert Tyler Shields at JupiterOne who called the 17.2 million attack “significant” and told ZDNet that the ability for a DDoS attack to reach that level of bandwidth exhaustion means that there is a significant backend infrastructure of either compromised hosts or hosts that have been scaled up with the sole purpose of sending malicious traffic.



