Fraud is ever changing. Fraudsters are continually evolving their craft to bypass bank fraud controls. As banks deploy AI and Machine Learning, fraudsters are employing their own machine learning to identify new and better ways to skirt controls.
And nowhere are patterns changing faster than in online account takeover.
A new study released this month by Castle, reveals 4 ways that fraudsters have shifted their patterns to exploit accounts online. Their study provides research that illustrates four new tactics cyberattackers are using to successfully take over accounts and exploit users.
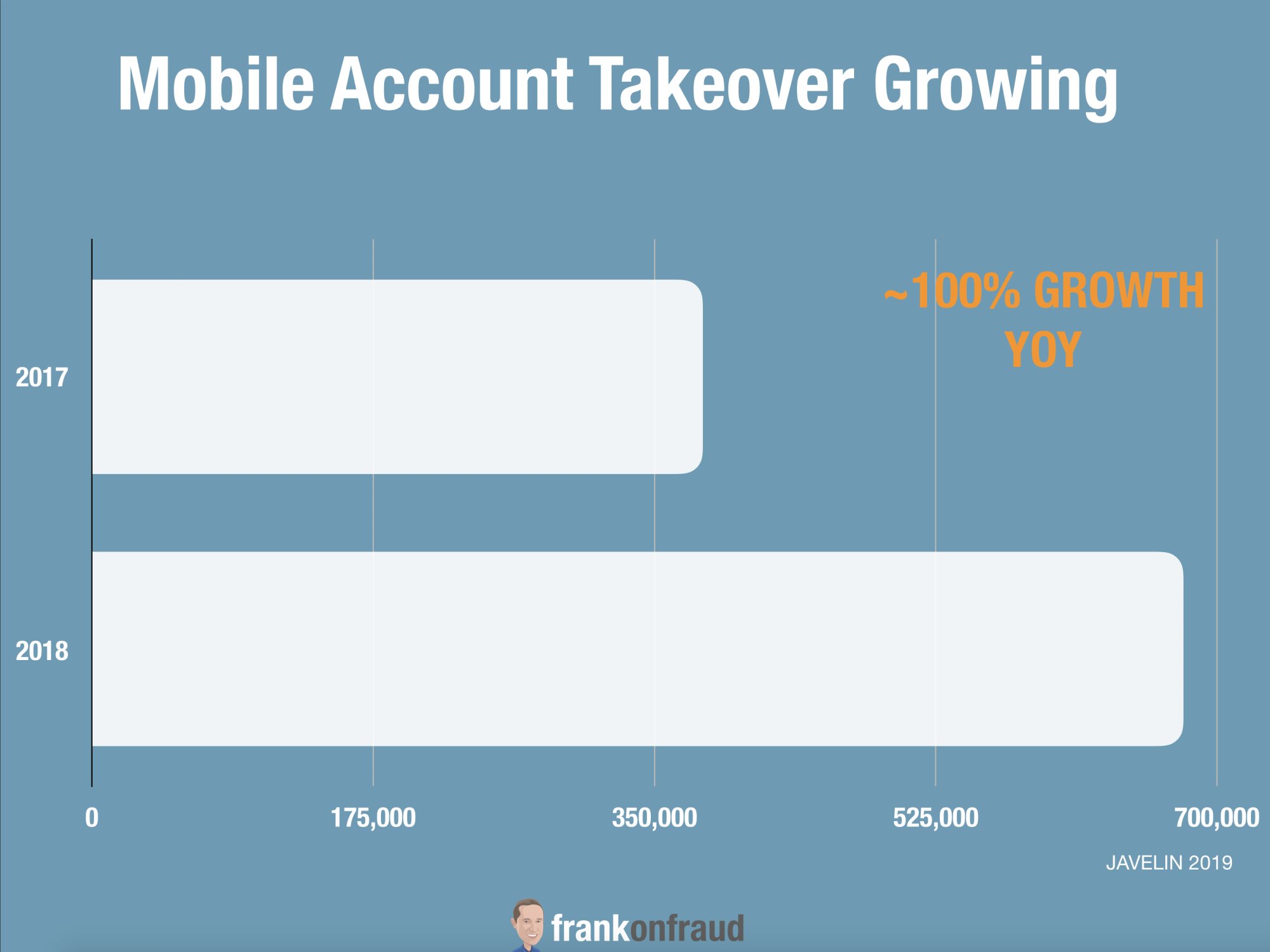
This is particularly important as Account Takeover attacks have been increasing rapidly over the last 2 years.
New ATO Techniques Have Success Rates As High As 30%!
According to the study, Castle has found loopholes that cyberhackers are exploiting with remarkable success.
Traditional success rates of account takeover attacks have been approximately .1%, but over the past year, Castle has discovered new trends in attack patterns with success rates as high as 20-30% in finding valid credentials.
The company’s research team was analyzing malicious login attempts of 100 million+ worldwide user accounts when it discovered this massive increase for some of its customers.
#1 – Appear Larger – Use More Users, More IPs
To increase their chances of blending in, fraudsters try to emulate as many different users coming from as many different places as possible.
They do this as a counterattack against rate limiting software such as Cloudflare, which companies can use to restrict traffic from an IP device once a certain number of login attempts are made.
In one case tracked by Castle fraudsters used over 80,000 different IP’s originated from 210 countries to spread out their hacking attack.
The company was unable to thwart the attack because there were simply too many IP’s and countries to identify and blacklist.
#2 – Appear Local – Use Local IPs
The second most common adjustment cited by Castle is the use of Local IPs that will not arouse a companies suspicion.
Residential IP providers, such as Luminati and Oxylabs, offer a pool of IP’s to users that belong to regular personal Internet providers, such as Comcast and AT&T. They enable users to select their physical location when buying server capacity helps to ensure it is as close as possible to the user to reduce latency and improve overall performance. But this allows an attacker to select the location they want the IPs to be in and rotate them as needed.
By using this technique fraudsters are circumventing companies Geoblocking rules so attacks can go unnoticed.
#3 – Appear Better – Use Fake Accounts to Improve Reputation
AI and monitoring tools have helped banks profile fraudster behavior from legitimate customer behavior.
Fraudsters have figured this out and have begun what Castle calls “Canary” accounts which they use to build up the reputation of an IP over a long period of time.
The fraudsters will use these fake canary accounts during the course of an attack to keep a good reputation.
They do several things with these fake accounts
- Identify if any blacklist are used by the company
- Identify what the logic of rate-limiting rules are so they can stay just below those limits.
- Identify the reputation rules of a company with such things as good to bad login attempts.
These canary accounts act as “test accounts” for the fraudsters to use while they create their own bots to circumvent the companies rules.
Appear Legitimate – Use Registration and Password Resets
Fraudsters are using information from companies’ websites to glean information from a companies database.
In a case that Castle sites, many sites reveal whether an email is in their database or not when a user requests a password reset. You may have seen the message, “Sorry, email not found” when trying to reset a password you’ve forgotten.
They also do the same for registration forms to see if users already exist in the database. By doing some filtering upfront the fraudsters are able to reduce their false positives and limit the potential for detection in the fraud departments.
If you would like to download the report, you can get it here.



