Gone in 6 seconds. Is it possible that hackers can correctly guess a card number, expiration date, postal code and CVV out of thin air and then use it to purchase goods fraudulently online?
Apparently, it is. And this impressive video shows the hacking program created to do just that.
https://www.youtube.com/watch?v=uwvjZGKwKvY
Students at Newcastle University believe they have stumbled upon a technique that hackers can use to exploit Online Merchants and steal hundreds of millions of dollars. And most surprisingly, the hackers would need absolutely no card information to do it.
In a study titled, “do-retailers-help-hackers-commit-fraud“, the students claim that differences in security solutions at different merchants create a hole that hackers can exploit.
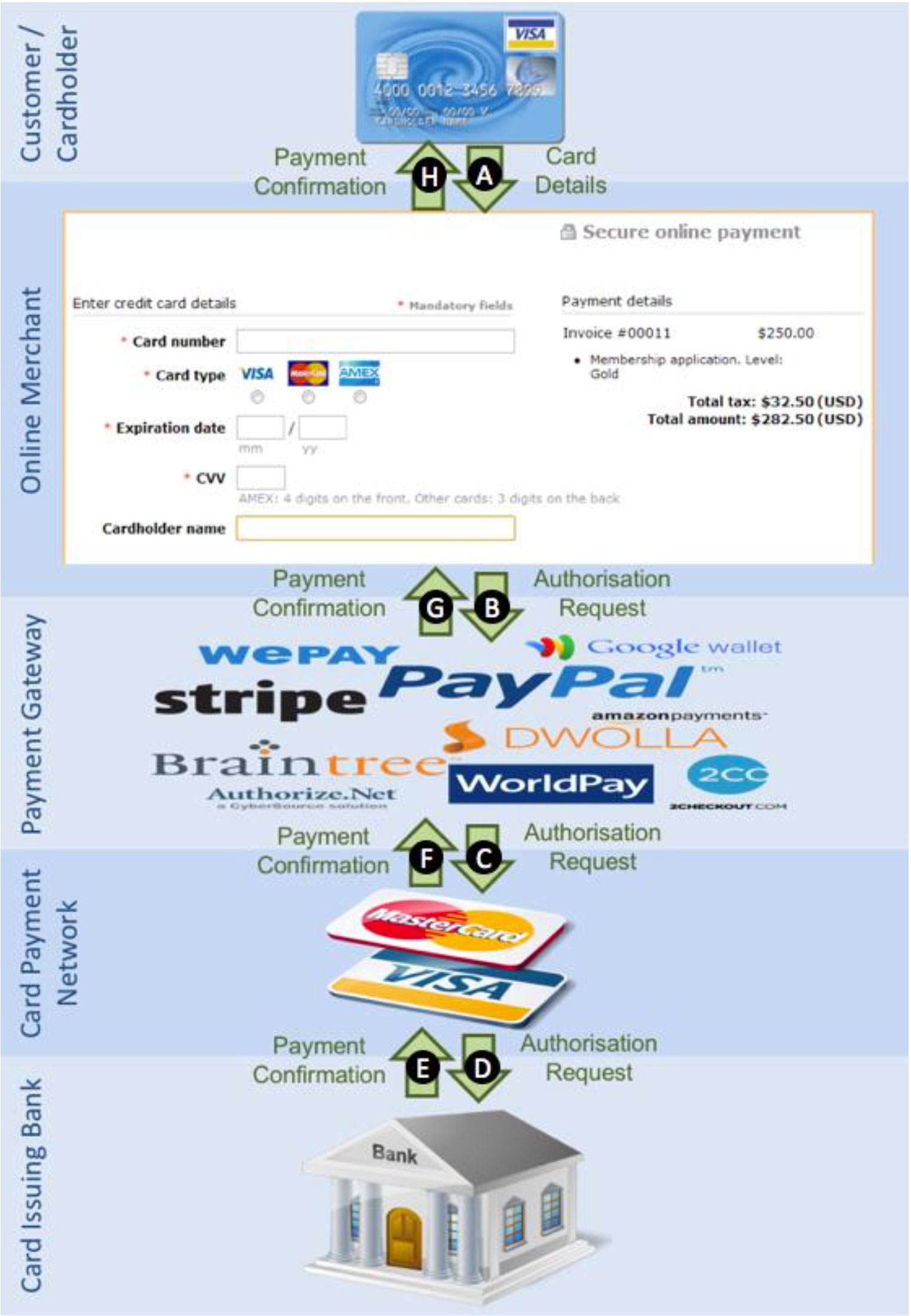
The students argue that an attacker can use these differences in websites to build a distributed guessing attack which generates usable card payment details (card number, expiry date, card verification value, and postal address) one field at a time. Each generated field can be used in succession to generate the next field by using a different merchant’s website.
By first gaining access to the card number, hackers could locate the correct expiry date with the program, them move to the finding the CVV2 value and finally the postal code. It would take tens and thousands of guesses but eventually you could be successful
It sounds so implausible that good credit cards and their associated details can be generated out of thin air. But apparently, the students were able to do it using their own card numbers and testing out their plan on hundreds of websites. It worked they say.
But they don’t stop there. They believe that the same technique was used to help online fraudsters steal 20,000 Tesco accounts and commit millions of dollars in fraud overnight.
Distributed Brute Force Guessing Attacks
The students claim that hackers are using the same technique that they have used for years to break into websites – brute force guessing attacks using BotNets. But instead of guessing passwords, they are guessing card numbers, expiration dates, postal codes and CVV2.
The researchers claim most websites, payments gateways and payment networks do not have any way to stop multiple attempts on the same card. They take advantage by using botnets to rapidly guess information across many websites until they get an order to go through.
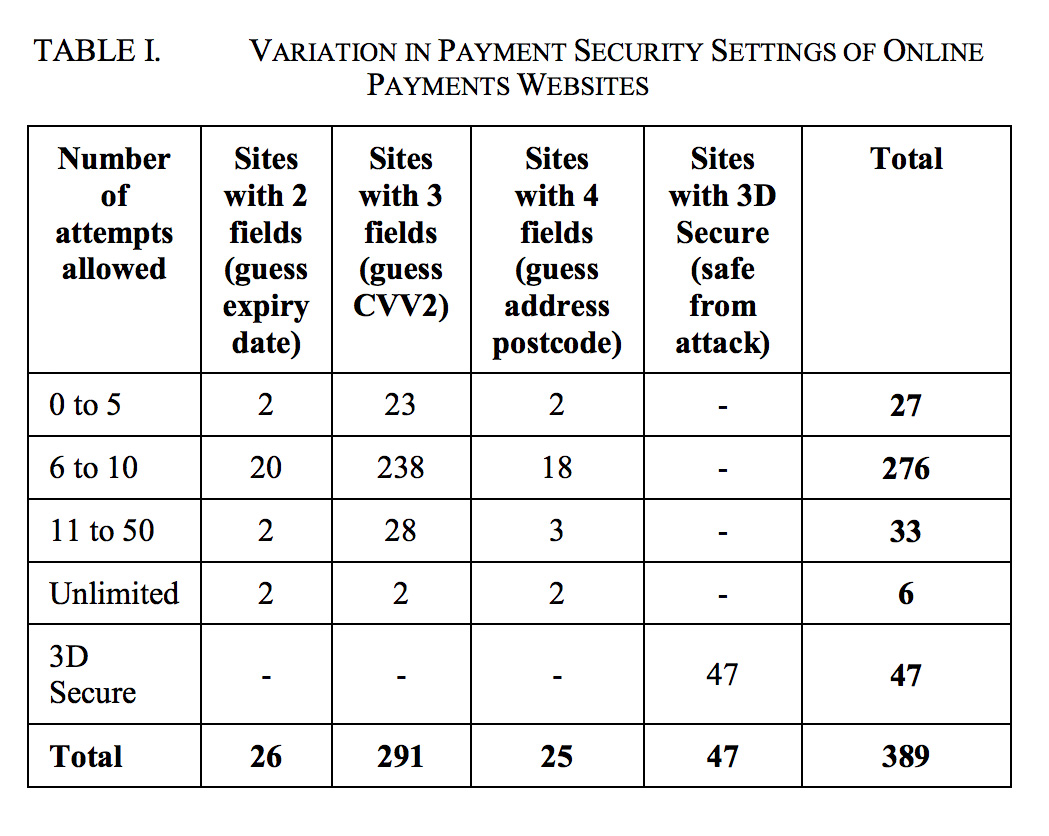
Since there were up to 4 pieces of information that needed to be guessed, they had to create distributed guess attacks for each piece of information across 400 different websites.
Based on the probabilities, some pieces of information are easier to guess than others.
For example,
- Expiration dates can be guessed within 60 tries since card issuers send out new cards with new expiration dates every 5 years (60 months)
- CVV2 values can be guessed within 1,000 tries as they are usually 3 digit numbers.
- Postal Codes = Here in the US it would take up to 10,000 guesses to generate the correct postal code
The researchers provided a diagram of the flawed card payment system that they indicate facilitates fraud
Their Brute Force Attacks Worked
The students claimed that their brute force guessing attacks were successful. They used their own cards, wrote some Javascript and launched the BotNet on hundreds of big online websites.
We implemented a set of software tools to carry out the distributed guessing attack, using the research team’s own cards to verify that it is indeed possible and practical to obtain all the information of the card. Included are seven Visa cards with a spread of PAN, expiry date, and CVV2 values. We selected 400 Alexa [12] top rated commercial websites for our investigation. These include many global websites such as iTunes, Google, PayPal, and Amazon. (The Researchers)
While the students did not have the BotNets guess the card numbers, they did try to guess the expiration dates, CVV and postal codes starting only with their own card numbers.
While they claimed to generate the correct expiration date and the correct CVV value on their cards, their study was more fuzzy around their success of generating the postal code.
My guess is that they did not although the did say that they used the “guessed details” they generated to ship money to someone in India.
The program works because not all sites are protected against brute force attacks like the one they created. They found that most sites did not
Problems with their Conclusions
I liked reading the study. I did find it fascinating. I think there were some underlying factors that the study failed to consider that would render these guess attacks useless.
- Postal Codes are far harder to guess than CVV and Expiry Dates. And most sites use the AVS which requires street number which would make it even harder.
- Falcon Blocks Would Likely Take Place. Thousands of attempts within a short period of time will drive the fraud systems at banks to start auto declining transactions. The research failed to recognize this impact.
- Merchants Order Review is sophisticated. Merchants order review processes often contain many negative file and velocity checks which they perform offline prior to shipping goods. Those would certainly trip up these multiple high-velocity attacks.
- Ship to Postal Code Is Important – Most merchants will flag or often deny merchandise from being shipped to any address that mismatches the CVV value.
- Guessing is simply too difficult – Buying breached card details is too easy and there is far too much of the information available on the dark web for fraudsters to do this.
Will Distributed Guessing Attacks Be Used Widely?
I am not sure this method will be in wide use by fraudsters. It’s far to easy to buy this information for $2 off the dark web than to try to create botnets to guess the information. Hackers that can build this sophisticated guessing algorithms would likely focus their time elsewhere.
As far as the ascertain that this method was used to perpetrate the Tesco Breach, I highly doubt it. There were 20,000 separate Tesco accounts used and that type of attack would likely involve many banks, not just an single banks accounts.
I applaud these researchers in exposing holes in the systems. Many of these were subsequently patched after their study.
I just don’t think this is the next big fraud trend. I could be wrong. I have been before.
Thanks for reading!