Rajesh Sharma received a call from someone claiming to be a recruiter. The caller said they got his number from a colleague who had recommended him for a promising new job.
When another call came in during their conversation, the recruiter suggested merging the calls to include Rajesh’s “colleague” in the discussion. Minutes later, Rajesh discovered $10,000 missing from his bank account.
This scenario is playing out over and over again in India where scammers are exploiting the “call me my code” option that banks use to send one time passcodes to their customers by calling the phone number of file.

How The Scam Works
I first read of the scam from Edgar Zayas of BioCatch who claims the scam is rising fast in India, with victims losing massive sums ranging from $10,000 to $114,000.
The scam first gained attention when the National Payments Corporation of India (NPCI) issued an urgent warning claiming that scammers were conning victims into merging calls with their banks automated OTP system and then capturing their OTP codes while they listen in.
Here is how it works:
Step 1 – The Setup Call
Scammer calls pretending to be a recruiter or event organizer, claiming they got your number from a mutual friend.
Step 2 – The Merging Request
During your conversation, they ask you to merge another incoming call that is coming to your phone, saying it’s from your friend who referred you and they want to give you additional information.
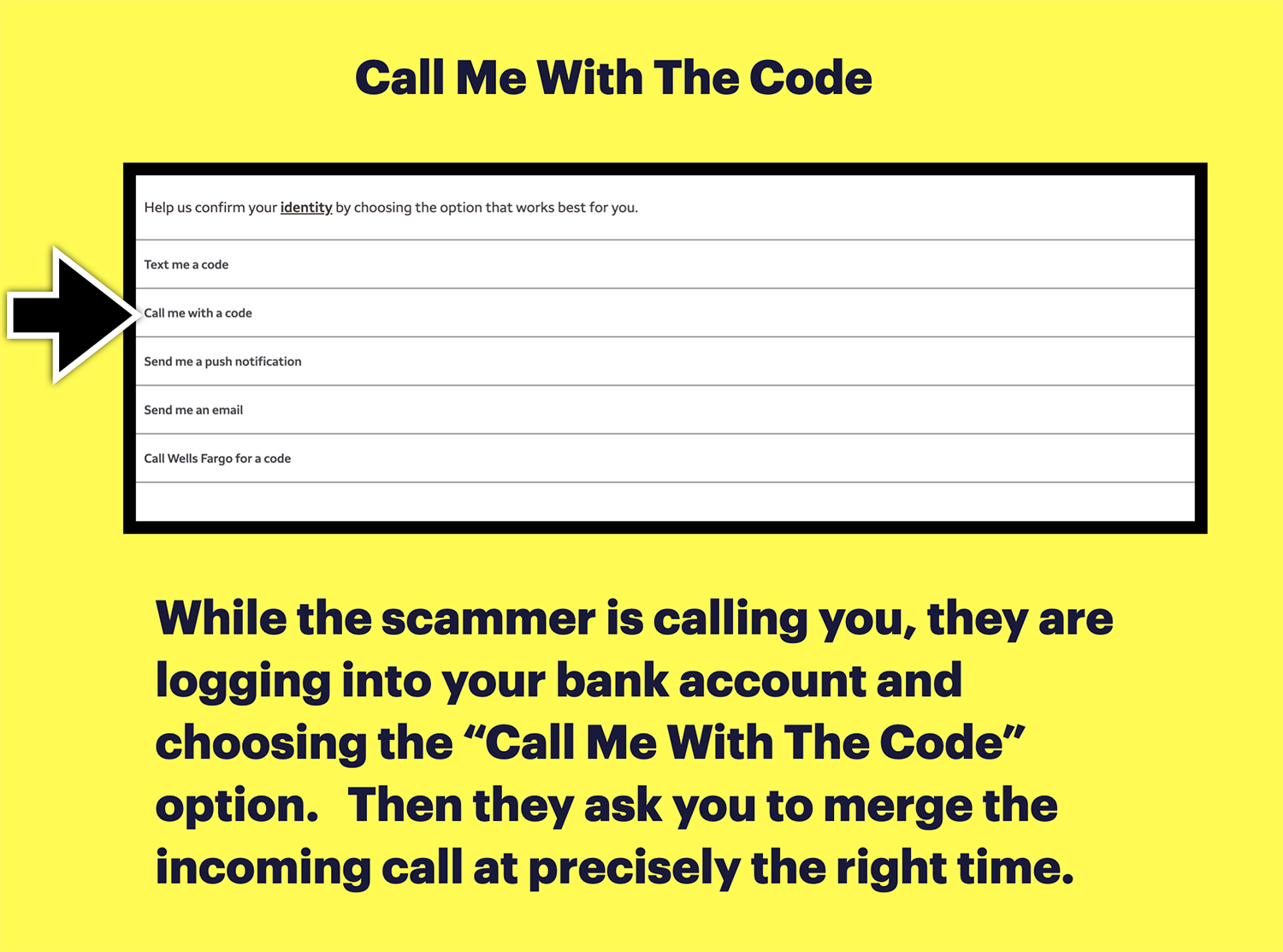
Step 3 – The Bank Call Trap
The second call isn’t actually from your friend, it’s a carefully timed call to your bank’s automated system sending a one-time password (OTP). The trick is in the timing so when you get the call, they will be listening in as the bank announces the OTP.
Step 4 – The OTP Capture
When you answer the bank’s automated prompts or you repeat the OTP, the scammer hears everything.
Step 5 – The Quick Heist
Within minutes, the scammer uses your OTP to transfer money from your account to theirs. Victims will learn of the scam because they get an automated alert, typically from their bank.
Why Its Dangerous – Banks Think Its Valid OTP Request
This scam is very effective because it bypasses the OTP process by leveraging a service most of us have forgotten about – the call me with my code option.
We have been so busy focused on stopping OTP’s that are sent via text, that we have neglected the exploits through the voice channel.

Banks will recognize the following transactions as authorized because a legitimate OTP was entered after the victim got the OTP over the phone. The bank doesn’t realize a scammer was on the call at the same time.
This Could Spread
Edgar Zayas, of BioCatch, points out that this scam could spread: “While the call-merging scam has gained significant attention in India, evidence of its occurrence in other countries remains limited… The underlying principles, however, align with global cybercrime patterns, suggesting potential adaptability to other regions.”

Not Just Limited To Bank Accounts
This technique isn’t limited to bank account OTPs. Any service that uses call-based verification can be exploited so this scam has potential across the board.
For example, scammers have posed as officials or VIPs to get targets to merge a “VIP call,” which was actually an OTP verification for apps like WhatsApp or Facebook. By overhearing those OTPs, they could hijack the victim’s social media or messaging accounts as well.
Watch Out For This In The US
Could this scam spread to the US? Absolutely. And my guess is that it probably will. The strategy of tricking someone into a three-way call to capture an OTP could be adapted wherever phone-based verifications are used.
Most US banks do offer phone call verification as an option for customers who prefer calls over texts, so the exploit is ripe for the taking here.
Be vigilant of this growing threat!



