In 2012, LinkedIn reported that about 7 million password credentials were hacked and breached. Well as it turns out, that number was grossly underestimated and was closer to 167 million according to recent reports.
To remedy the situation, LinkedIn forced password resets on all affected accounts that they could locate. Problem solved right? Wrong.
The problem is actually just starting for the 167 million people worldwide that had their credentials stolen. You see, 55% of consumer use the same passwords across all of their websites and accounts. That means that the hackers potentially have access to 80 million consumer’s bank accounts, their uber accounts, their gmail accounts, paypal accounts, possibly even their GoToMyPC account which means even their personal computers are subject to vulnerabilities.
When the Hackers Tapped Into LinkedIn, they tapped into a GoldMine worth potentially billions of dollars in future fraud. To this day those stolen login’s are likely being used to access millions of consumers online services.
The Old Account Takeover Has Changed to Something Far More Automated
Only a few years ago, Account Takeover was a fairly manual process. Fraudsters would call operation centers and try to fool the customer service associate into changing the address and then sending out new cards. It was common but losses were not high. Account Takeover was consistently about 5% of a bank’s fraud loss.
Today, Account Takeover is far more automated. By leveraging stolen login credentials with scripted code called BotNets, the fraudsters are able to direct hundreds of thousands of test against many website simultaneously. For example, they could run a consumer’s LinkedIn email and password combination against Uber, Gmail, Yahoo, PayPal, Ebay, Amazon and thousands of other services in less than a few minutes and know which accounts they were able to get into. These are validated credentials and they can be sold for hundreds or thousands of dollars on the Dark Web as I wrote about last week.
More Automation Leads to Higher Account Takeover Losses
So is this far more automated way of perpetrating ATO leading to higher losses. You bet it is.
The Auriemma Group recently published their Debit Fraud Report and found that ATO fraud was up a whopping 280% last year. Read it here – Debit Fraud Account Takeover.
The Auriemma Group indicated that Account Takeover Fraud was up 280% in 2015. I think that is just the beginning a long and steep climb in losses that we will see from the category.
But that is just the beginning. This year 2016, from what I am hearing will prove to dwarf the rise in losses that we had last year.
Account Takeover is Rising Because BotNet Attacks Are Spiking Upwards
ThreatMetrix released their Quarterly Benchmark report and indicated that they had thwarted over 311 million Botnet attacks in the first quarter alone – The Report.
I have seen these botnet attacks increasing myself so I was not surprised at the number, however what is more concerning is that the attacks are up over 35% this year over last years already incredibly high number.
BotNet attacks as measured by ThreatMetrix are up 35% mostly against financial institutions for setting up new accounts or taking over existing accounts.
Account Takeover is Rising in 2016 Because EMV Was Implemented Last Year
Account Takeover increases is just part of the normal cycle of EMV implementation. In other regions of the world sharp increases in Account Takeover occur as a result of fraudsters moving on from cards when counterfeiting is made more difficult.
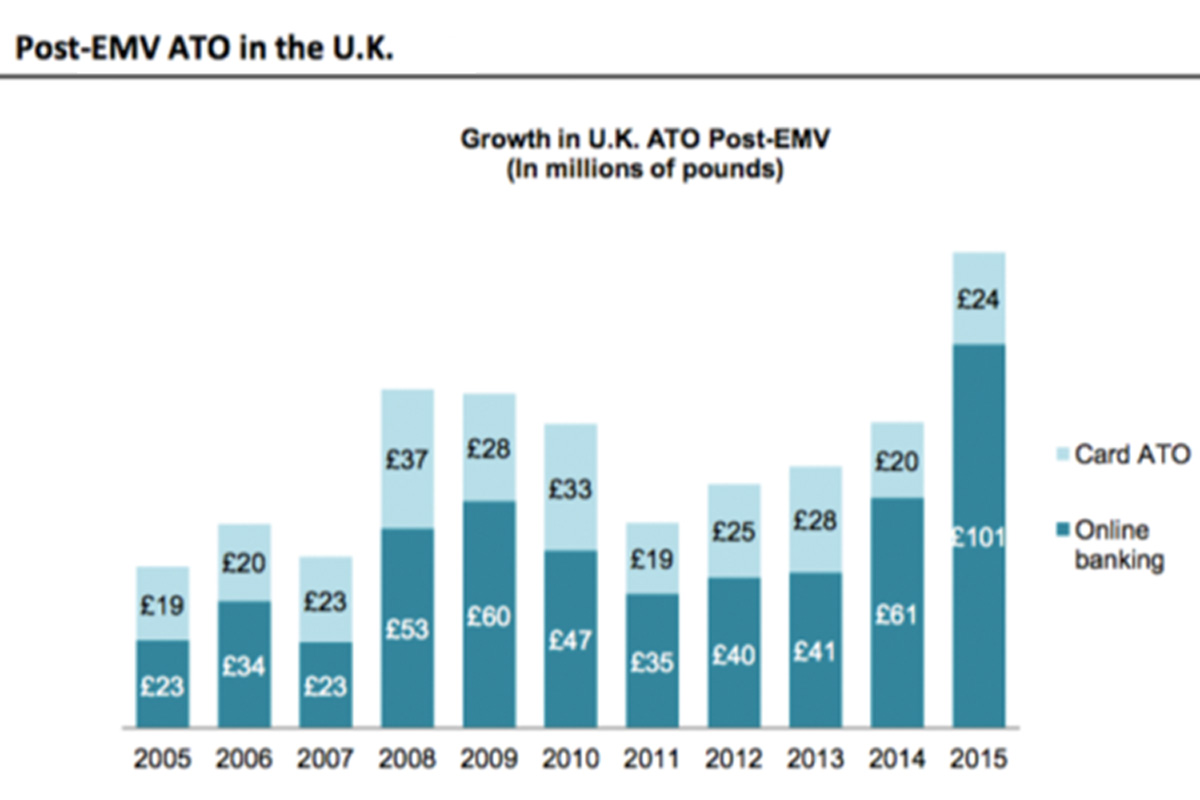
In the UK for example, since Chip and PIN was implemented, Account Takeover losses have increased year over year for the last 10 years.
The greatest segment of increase was the move to taking over online banking credentials to send fraudulent Wire, ACH and payments to mules or third parties.
In my conversations with US, issuers, Banks and Telecom providers, I am being told that fraudulent login attempts post EMV are hitting them hard. In some cases, thousands of accounts can be accessed with stolen login’s overnight forcing significant operational pain even when those accounts are not used immediately.
Account Takeover is Increasing Because Credentials are Worth Far More Than Cards
Fraudsters are moving from cards. Why? Because while they are crooks they are also business people and they always direct their scarce resources to that which provides the greatest return. Right now the math clearly points them in the direction of online credentials.
Reports by LogDog indicate that fresh card numbers will sell for $2 but after several weeks when the cards might have been blocked they only fetch .50 cents.
Stolen and Validated Login Credentials can fetch hundreds of dollars if the balance on the account is high enough.
Alternatively, login credentials can range from $1 to over $1,000 based on the balance or availability of funds on the account. Clearly, stealing login credentials is more lucrative to the hackers, the fraudsters and the mules.
The New Gas Station $1 Test
Back in 1991 when I was first analyzing credit card fraud for models we were building I noticed something unusual. I noticed that there were $1 transactions to gas stations immediately before the big fraud activity started.
What I was seeing in the data were pre-authorizations at the gas station where the fraudsters would go to test the card to see if it worked before going to places like Circuit City to buy their computers. It was smart way for them to see if the card worked since they would never get caught because there are no cashiers at the terminals.

Fraudulent login’s are oftentimes the new $1 test at the gas station. Most of the successful attempts are not used right away. They are used later after the credentials have been sold.
This fact creates an opportunity and a dilemma for banks. Since the fraudsters are not using the credentials right away, they will test tens and thousands of credentials at once but that can bury the bank in alerts that may or may not be false. Banks are struggling with how to process all of the fraudulent login’s while not impacting all of their customers.
New Technologies Are Getting Booming
Thanks to the fraudsters activities, new technology companies are sprouting up to help the industry solve the problem.
Device profiling companies like Iovation, ThreatMetrix, InAuth, have created consortiums and use sophisticated algorithms to spot botnets, validate browsers and mobile devices and to alert other banks when there is suspicious login activity across multiple websites.
Other companies like Guardian Analytics focus on providing banks monitoring technology for online account sessions. And platform providers like Fiserv provide technology to stop account takeover and fraudulent wire or payment request in realtime.
These cool technologies are helping stop the rise in fraud. But for some foreseeable future I just see it growing.