The Dark Web. You can’t see it. Maybe you have no way to even access it but it is there lurking and impacting you in ways that you don’t even realize.
If you’re an average everyday consumer you probably won’t be able to access the Dark Web but you need to know that it’s a veritable Garage Sale and some of your most personally valuable information is for sale for less than prices you find at the 99 cent store. For a couple of bucks fraudster’s can purchase your credit card, debit card, social security number, driver’s license, mother’s maiden name, IRS Tax Filings, username and password combinations to your bank accounts.
When I think of it. I am absolutely terrified of the ramifications. Someone could literally drain my bank account while I am asleep. And they could probably make it look 100% legitimate because they have so much information on me.
How Do You Get to the Dark Web?
The Dark Web is not visible to Google since it is a series of encrypted networks between hidden servers and clients. So you need passwords and the right software to be able to access it.
Just like a speakeasy in the old prohibition days, you need to have the right information of knowing where to look, and then what to say once you knock on the door.
For example to access the Dark Web, you can’t just use your normal browser you have to use special anonymous software like TOR which lets you can download off the internet.
Once you have the right software, then you need to have the addresses of the locations you need to access. Think of the days before google and how confusing it was to find stuff. Well the dark web can be that confusing too since it not all in one nice neat place.
Hidden links might look something cryptic like this list from the Hidden Wiki.
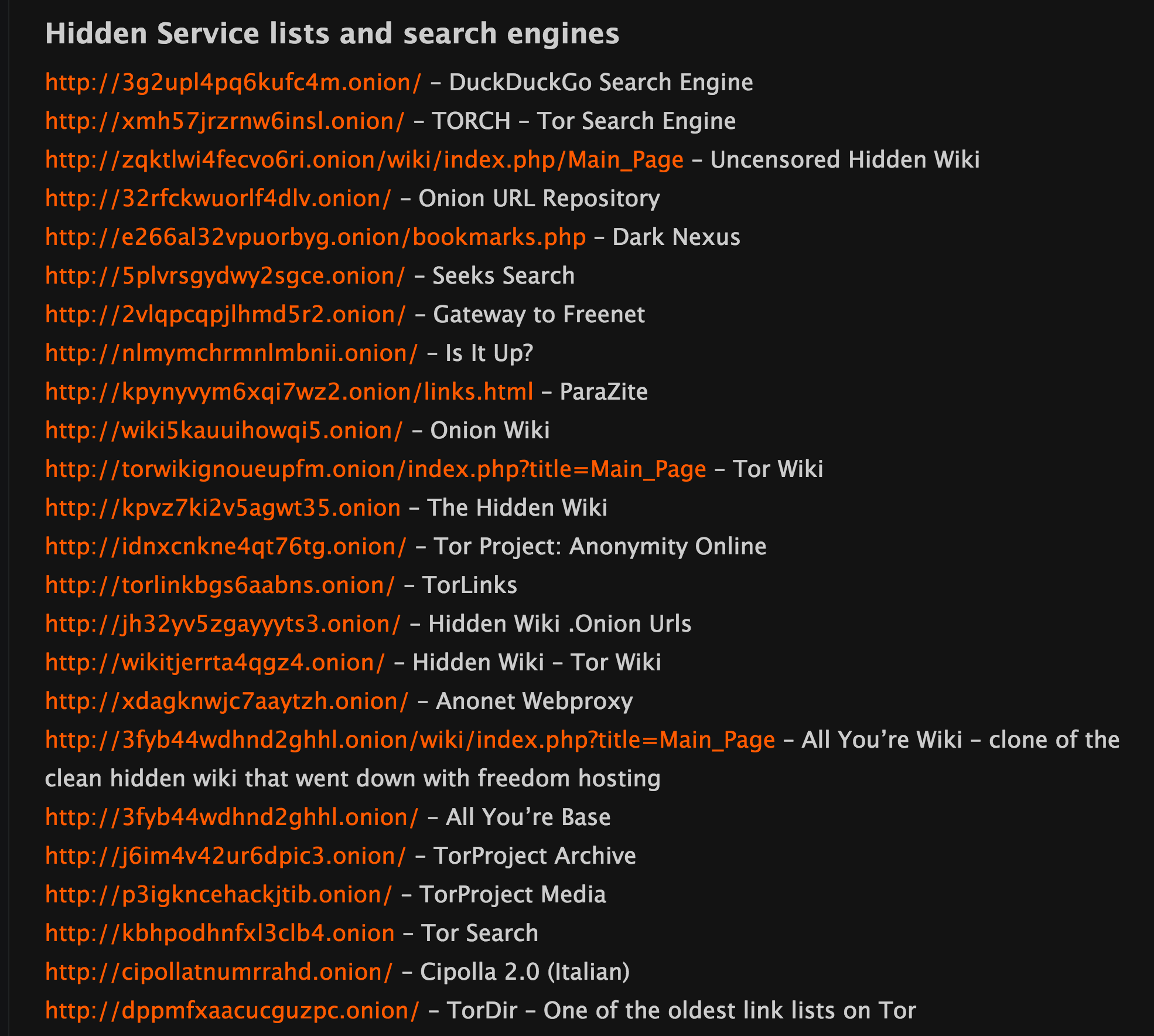
The Dark Web has all sorts of people on it and some of it involves buying or selling illegal things. Their are white hat hackers and law enforcement trying to stop things like drug trafficking, weapon sales, human trafficking, and sale of personal information. And then on the other side you have all the people trying to sell those illegal things. In the end, neither of them really wants the others to know they are there.
How Does the Buying and Selling Work (The Target Example)
As I mentioned earlier, the Dark Web is like a big garage sale. I read a great article on how the Black Market works on the Deep Web. Do you remember the Target breach? Hundreds of millions of cards were stolen and they were eventually sold through the black market. The Target Breach was one of the biggest reasons that the US Card Fraud Losses spiked in 2014 and caused the US consumer to be the biggest target of fraudsters across the world.
You can read the great article here – How the Black Market Worked with Target Stolen Cards.
At the time, 40 million credit cards were breached at target and the asking price on the Dark Web was $40 a card. Over time those prices dramatically dropped since the market was flooded. You can see the price list here from TripWire
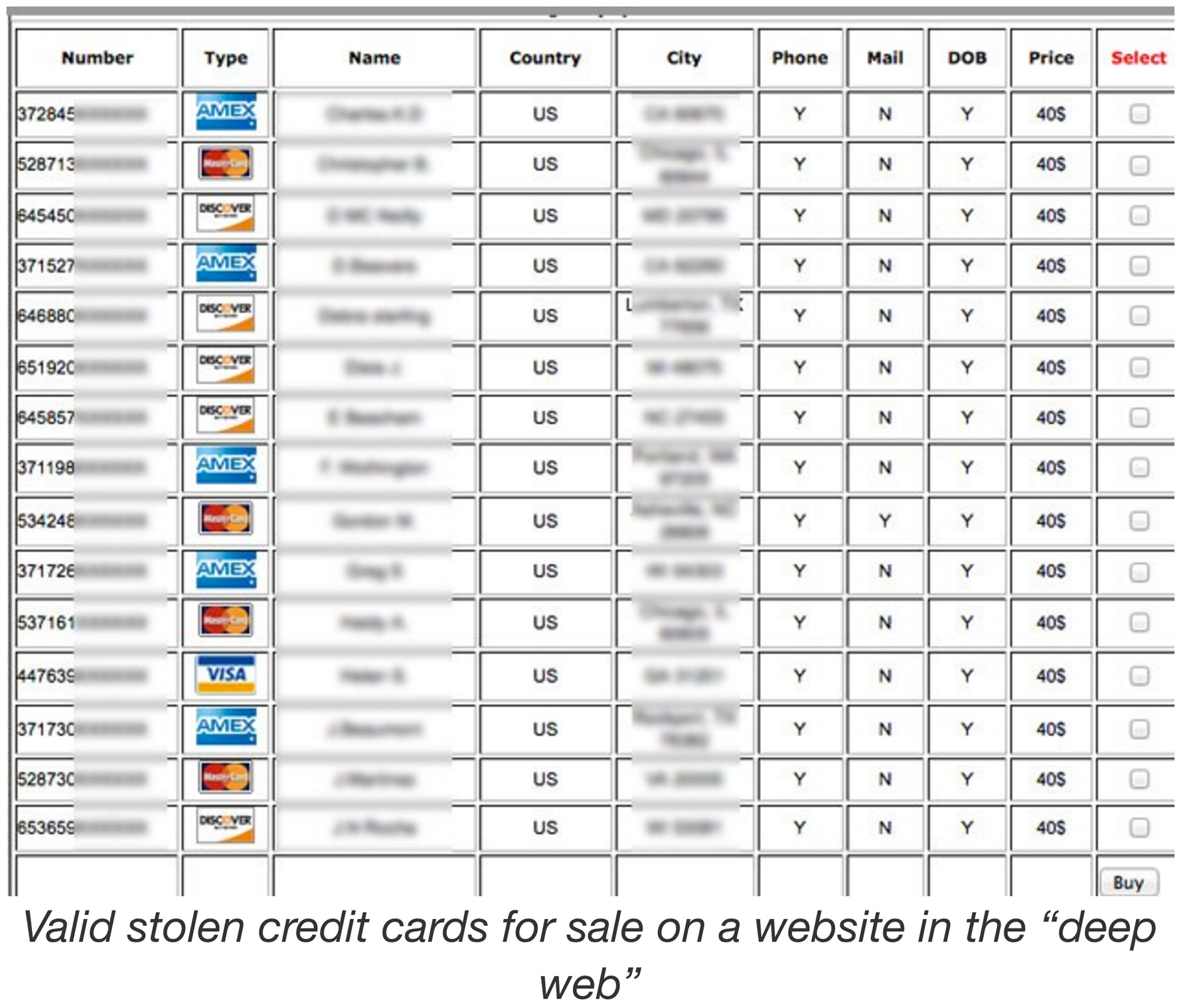
Most of the cards on the Dark Web come with a guarantee. If the card does not work, you get to come back and get another card for free. That is some great customer service right there. Oh and you usually pay with BitCoin’s by the way. They won’t accept cards.
Once a fraudsters buys stolen card information they can primarily use it in 3 different ways to turn it into cash.
They load gift cards – They use the credit cards and load money onto gift cards which they can then sell for cash.
They buy merchandise online using mules – Using sophisticated shipping with third party mules or unoccupied houses they send merchandise purchased on stolen cards to places where they cannot be detected.
They sell merchandise on Ebay or Craigslist – After they receive the merchandise they turn the goods into cash by selling them at a discount on CraigsList or Ebay.
How Much Can you Buy Information For?
Buying stolen information is ridiculously cheap. Sometimes it is pennies. And it is just getting cheaper since there is a glut of stolen information that is for sale. Supply and Demand dictates prices on the Dark Web.
Billions of pieces of breached data are being added annually to the Dark Web. Gemalto estimates that 245 million pieces of breached data were added the first half of the year. That is about 16 records a second.
Do you want to see something scary? Check out this counter that shows how many records are being detected in real time – We are currently running at over 4.7 billion records since 2013. Data Breach Index Counter.
As a consumer living in the US, you have to assume that every credit card, every debit card and your login’s to ever website and app you use have been compromised. Statistically, it just makes sense.
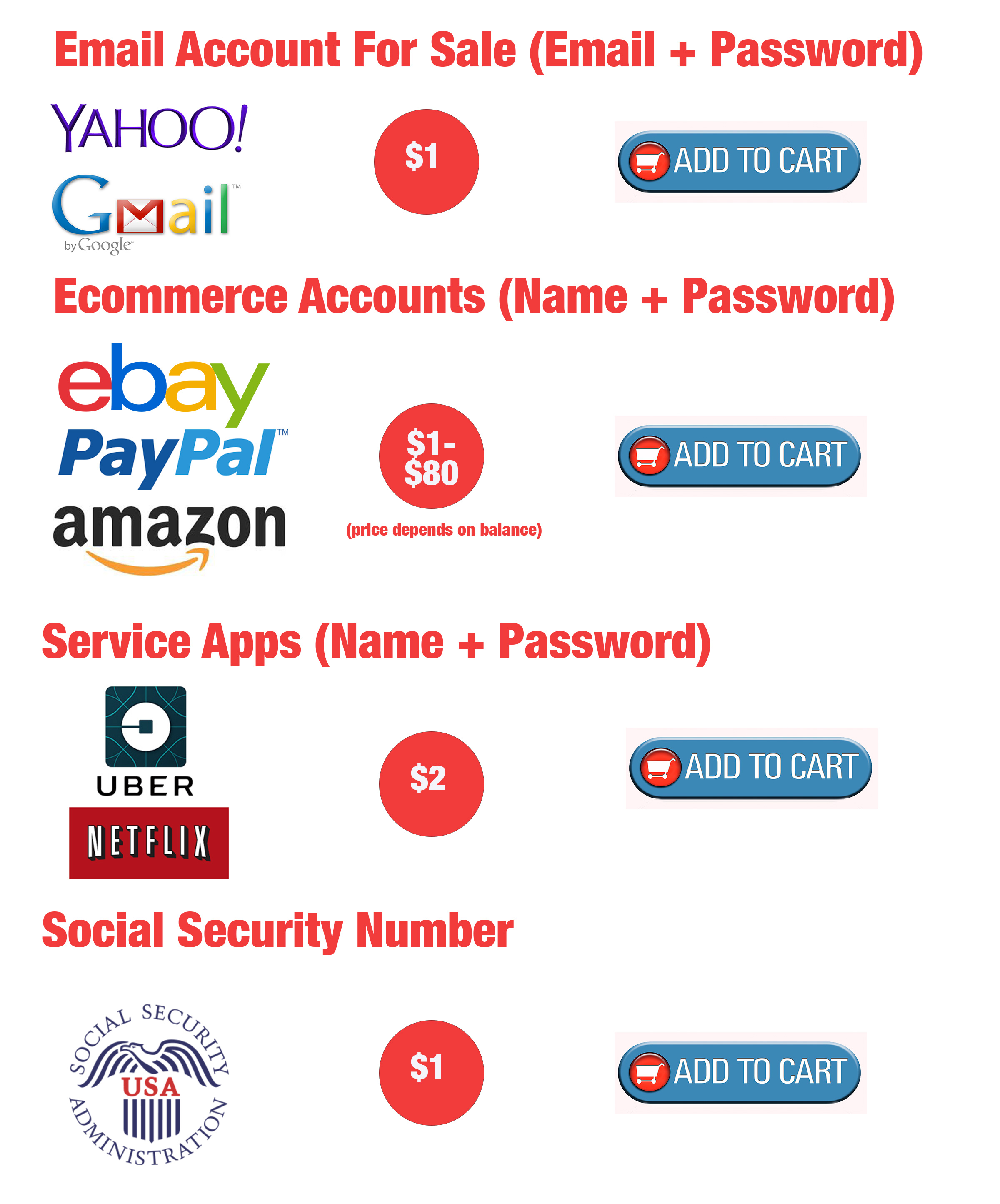
Like I said, information is cheap. I researched it a bit and found this information on sales price from an anti hacking company called LogDog. They have white hat hackers that research the web for stolen information.
Here is a sample price list that I compiled from their research. Pretty cheap huh? I was surprised.
What is Hot in the Market?
The trends on the Dark Web and what sells is changing quickly and financial services and online retailers are getting hammered.
Years ago, fraudsters wanted cards. But with the implementation of EMV, they have shifted now to new techniques and what is selling is login credentials. The fraudsters want login credentials to any account you have because the payoff is so big. This includes login’s to your email accounts, bank accounts, service apps, internet service providers, your wireless account. Anything they can get.
Think about it. If a fraudster can get your gmail account and login they can test that same information across many different sites since most people use the same email and password combinations across various sites. That email becomes tremendously valuable in taking over your entire digital identity.
BotNet Attacks Make Fraudster’s Efficient
I am hearing from sources that banks and other companies are experiencing significant bot attacks on their online banking account customers where the fraudsters are creating automated programs to test thousands and thousands of credentials until they find one that works.
When they find credentials that work, say on your Wells Fargo account, they can either sell those on the Dark Web based on the balance of the account, or they can use it at some point in the future.
The sheer volume of these successful botnet attacks are so high that companies may not even have the resources to be able to change the passwords on all the affected. If they did they might have to reset passwords several times a year.
Authentication Needs an Overhaul
There is only one answer to this problem. The old ways of authentication – user names, passwords and 2 factor authentication don’t work anymore. As you can see they are almost useless against the onslaught of attacks from hackers and fraudsters.
We are at the point that we need to start evaluating better authentication strategies such as biometrics or more fail safe methods that can confirm identity of a person without relying on data that can be stolen.
We have reached that inflection point which dictates that the ROI is worth it because the cost are so high.
Thanks for reading. Let me know your thoughts on this subject. It is quite interesting to me.



