Palo Alto Networks research team – Unit 42 – is warning that BEC as a service is rising and that Business Email Compromise continues to be one of the biggest threats today.
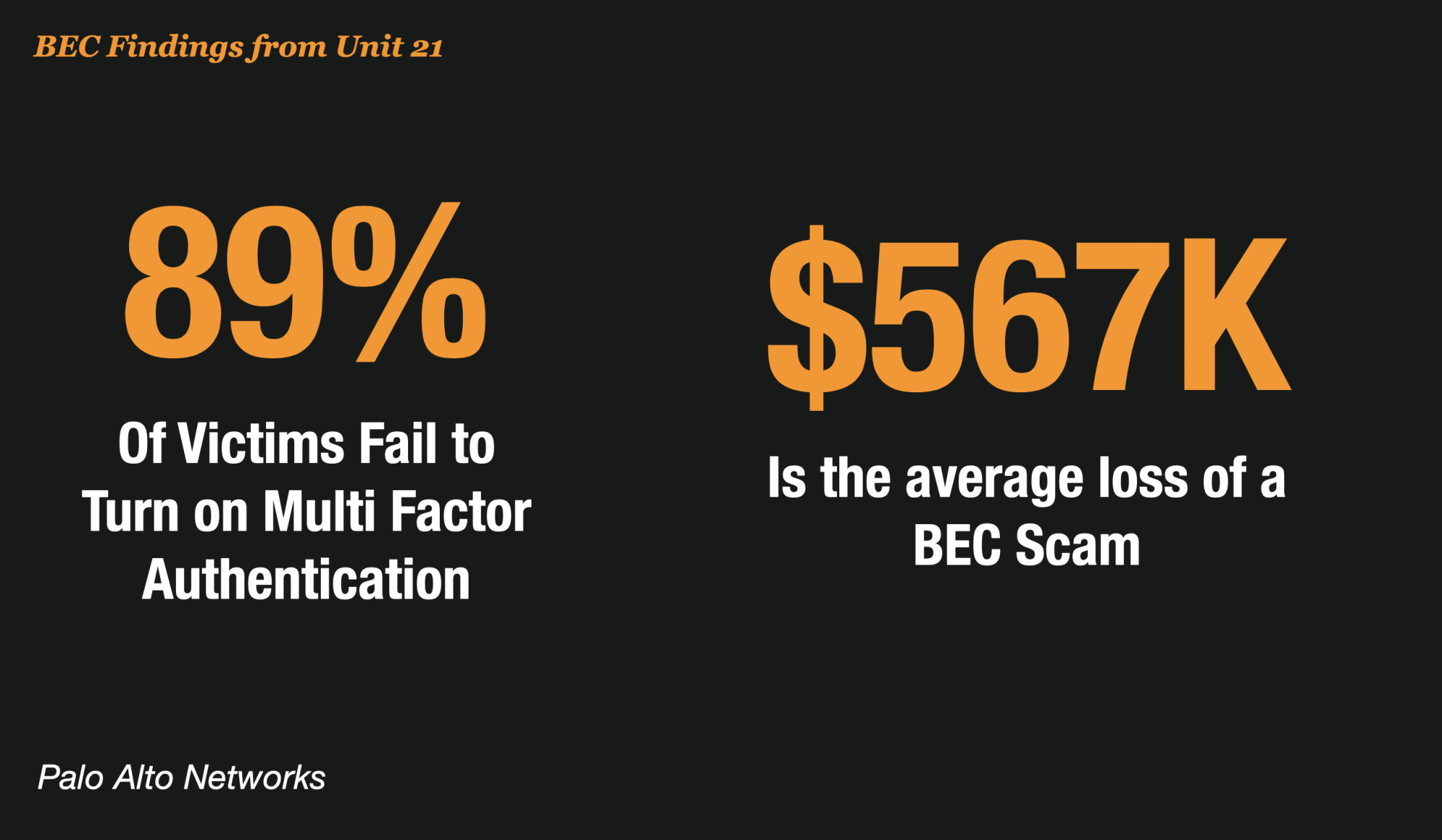
According to the report covered on ZDNET, the security team pored through hundreds of BEC cases, finding the average wire fraud attempted was $567,000, and the highest was $6 million.
Among the hundreds of BEC cases Unit 42 tackled since the beginning of last year, researchers found that 89% of victims failed to turn on multi-factor authentication or follow best practices for its implementation
Many Victims of BEC Do Not Report
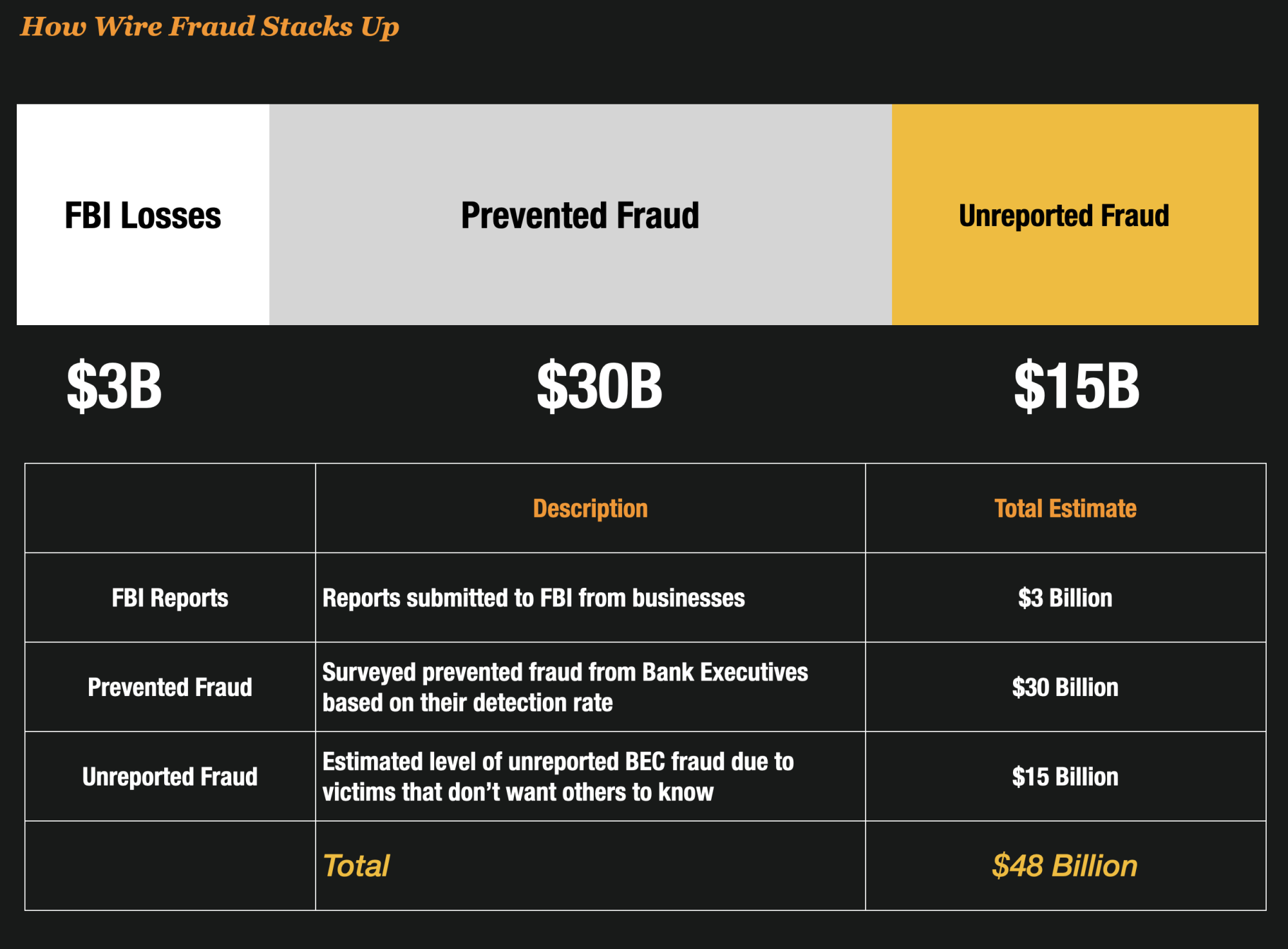
The FBI reports that BEC costs American’s more than $1.8 billion a year, making it 64 times more damaging than ransomware. In other years, it has run as high as $3 billion annually.
But experts at Unit21 believe that many victim businesses do not want to suffer reputational damage so many BEC crimes often go unreported making BEC a silent crime in most cases.
Indeed, my estimate of Wire Fraud – the predominant financial vehicle used in BEC – is closer to $48 billion annually.
Because so much of wire fraud is social engineering schemes consumers and businesses often feel conned or embarrassed that they were victimized. Because of this, they will often not report it.
My estimate is that most wire fraud (where there is a loss) actually goes unreported because the consumers are embarrassed or the business does not want to look like they have been conned.
Fraud As A Service Grows in BEC
According to Unit 42 experts, BEC is becoming increasingly more sophisticated and certain players are selling their services.
ZDNet reports that in an interview with Jen Miller-Osborn Deputy Director of Unit42 it is a worrisome trend.
“Similar to ransomware, we’re seeing an increasing number of attackers getting into BEC, and we’re also seeing it mature into — like Ransomware-as-a-service — BEC-as-a-service. They’re becoming more tech-savvy. They’ve been in the commodity space and are starting to include publicly disclosed vulnerabilities. They’re becoming more professional.”
“With everyone working remotely, there are people who may not have gotten into BEC before who now, just like ransomware, they decided to shift into to make money. And I think the issues that we see with how difficult it is to stop these ransomware campaigns effectively also points to how difficult it is for BEC, or even harder because BEC involves a lot of social engineering components that you don’t typically see with other attacks,” she said.

“They’ll actually get on the phone and call people and try to get them to do things. They have money mules in other countries to help them move the money around. It’s a lot more people-based, and in many cases, a lot of BEC scams don’t involve any malware, so there’s nothing that you could have seen.
To read more on the issue, you can visit some of the great research from the folks over at Unit42 here.



