As the pandemic emerged in 2020 and lockdowns began across the world, consumers shifted online to get their goods and services. Online spending reached 18% of total retail volume compared to only 14% in 2019.
And the flood of online shopping and activity was great cover for fraudsters who ramped up their online activity significantly as well.
DataVisor analyzed 128 billion online transactions from over 2 billion users in 2020 and discovered that account takeover is the most common attack – comprising 70%- 90% of fraud attacks. Account takeovers grew over 2020 as the pandemic raged.
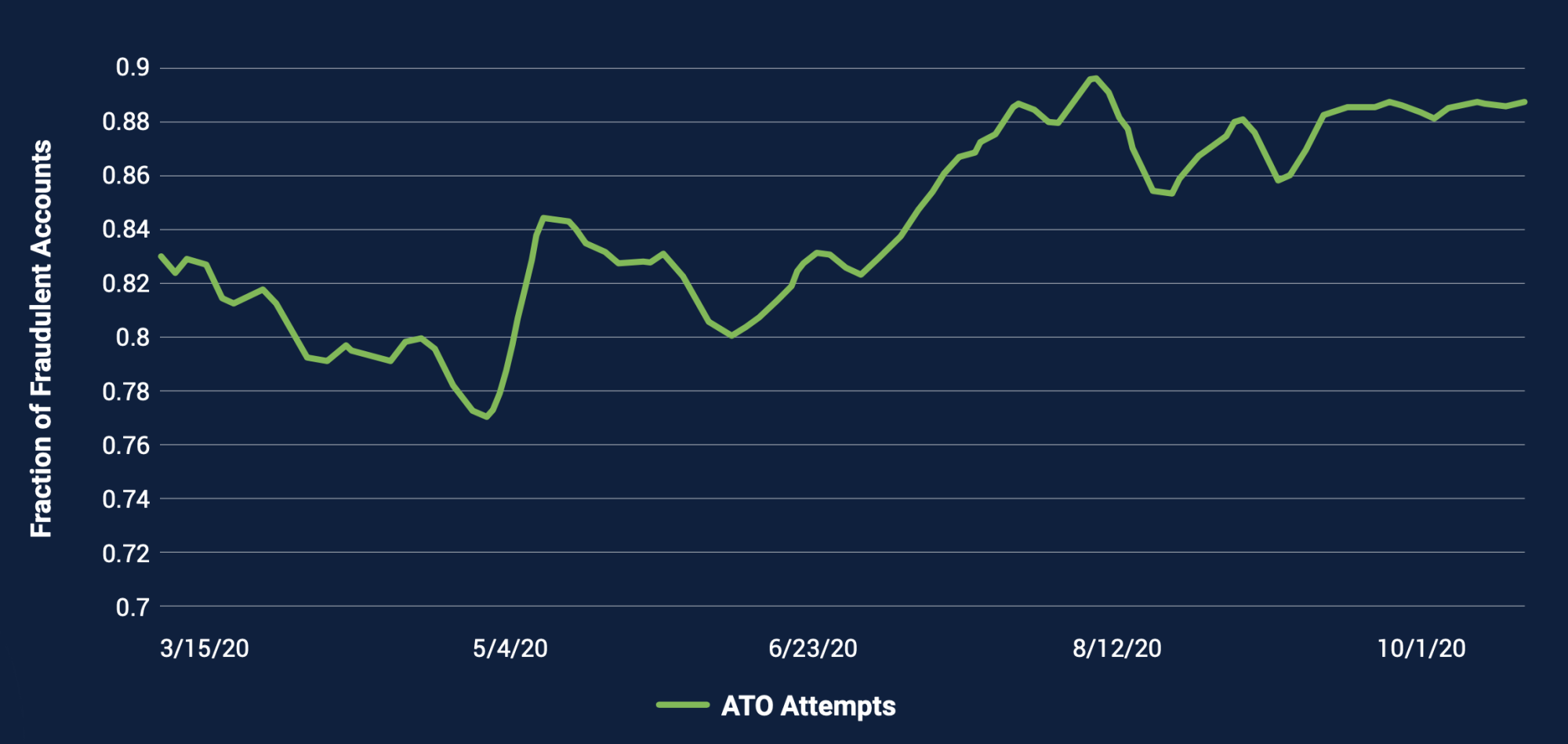
The report provided some interesting key takeaways and statistics that paint a picture of the ever-changing patterns of risks online.
#1 Desktop Platforms Are Choice for Fraudsters
DataVisor determined that the fraud rates for mobile platforms was only .5% while the fraud rate for desktop platforms was significantly higher – 7.4%.
The fraudsters platform of choice – Windows with over 50% of fraudulent users originating from Windows operating systems.
#2 – Rooted or Jailbroken Devices Have 22 Times the Fraud Rate
DataVisor research found that 22x more events occur via rooted or jailbroken devices, both of which appear to be much more active than non- jailbroken or non-rooted devices. This is likely due to fraudsters using them to control multiple accounts at scale.
#3 – Fraudsters Re-Use Information
DataVisor research shows that up to 40% of scammers on marketplace platforms reuse phone numbers or email addresses in defrauding their victims (though they may be hidden in images or obfuscated using special characters or similar-looking characters).
#4 – 100% of Fraudulent Attacks Use Automation At Some Point
DataVisor research indicated that fraudsters are highly efficient in their processes.
- At account registration time (social, E-commerce, marketplace sites), 55% to 90% of fraudulent accounts use scripted names, nicknames, or email addresses.
- At least 30% of fraudulent accounts originated from IP ranges associated with data centers, VPNs, or proxies on platforms that experience massive coordinated attacks
- Across all platforms, 40% of fraudulent accounts exhibit “spiky” behavior with sud- den rapid succession of activities (a sign of scripted behavior)
#5 – 1 in 50 Bot Attacks Can Solve Captchas
Surprisingly, those annoying captchas are not infallible. DataVisor determined that 2% of fake accounts have been confirmed to solve CAPTCHAS, bypassing basic attempts at blocking automated activities.
And there are lots of false positives. Captchas can have a false positive rate of 8%, and that rises to 29% when the Captchas are case sensitive.
DataVisor Recommends a MultiLayered Approach
According to experts at DataVisor, they recommend using a comprehensive multilayered approach to uncover highly sophisticated attacks early and at scale can allow companies to stay ahead of the evolving fraud curve and thrive in the digital economy.



