It isn’t often that your hobby and your career collide but recently that is just what happened to me. Photography is my hobby. Fraud and Security management is my profession. So when I learned that cameras were used to launch one of the largest cyber attacks in history, I was intrigued.
It All Started with A Blog Post
One of my favorite blogs to read is KrebsonSecurity. Brian Krebs, a former award winning journalist with the Washington Post and cybersecurity expert, always post interesting articles on the dark underworld of hackers and interesting security topics on a daily basis. With his many contacts throughout the industry he is usually first to report on new cyberattacks and security trends.
Recently however, Krebs really pissed off some hackers in Israel. The company was vDOS and apparently he reported that they had made a ton of money ($600,000), by conducting over 150,000 Distributed Denial of Service (DDoS) attacks to bring websites down. In his report, Krebs discovered that they alone were responsible for a vast majority of the organized attacks in the world and would concurrently run thousands of attacks across the entire internet
In just four months between April and July 2016, vDOS was responsible for launching more than 277 million seconds of attack time, or approximately 8.81 years worth of attack traffic. Let the enormity of that sink in… Brian Krebs
Then The Hackers Turned the Tables on The Blogger
A week after Krebs published the report, hackers turned the table on him and launched the largest Denial of Service (DDoS) attack in history against his site. He does not know who launched the attacks but he has suspicions
His site went dark for 24 hours while it was attacked. And the attack grew stronger and stronger reaching 620 gigabits per second. Every minute that passed by they were pushing 37 Terabits of data request through and his site couldn’t handle it. If you try to fathom how disruptive the attack was just imagine 50,000 to 100,000 simultaneous HTML request to your website every second. No site could handle that massive amount of data.
Thankfully, Google stepped in with Project Shield to keep his site up and running. Project Shield was formed to protect journalist from censorship caused by things like denial of service attacks.
A Robot Army Rises From The Internet of Things
We live in a world of connected things. And everything seems to be connected through a single highway – The Internet. Those things include phones, cameras, thermostats, lights and even the locks on your home. Gartner projects that there are 6.4 billion devices connected to the internet and that the number is growing every single year.
These connected devices spell trouble for fraud and security though. Because each device is connected to the internet it can often become the easiest point of entry for fraudsters or hackers. Once the hackers access the device they can enslave the device as a robot to do simple things such as repetitively hit a website over and over again.
Connected Devices Can Be Used as Pawns in DDoS Attacks
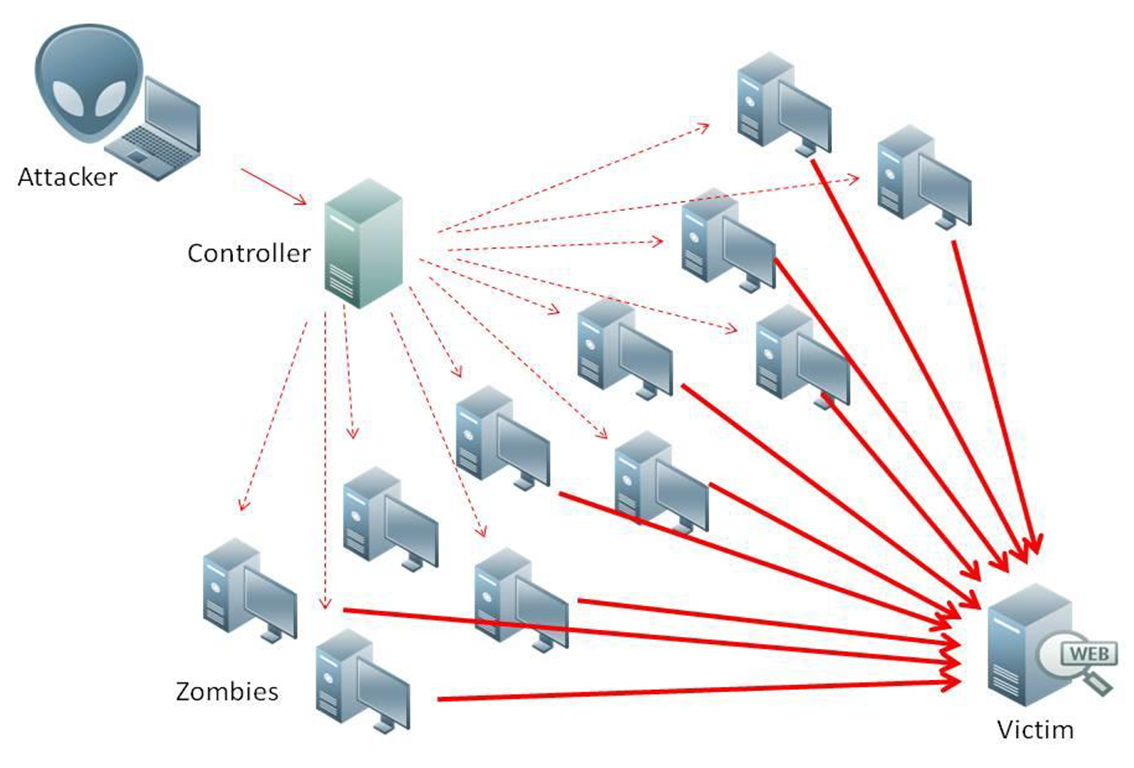
In the case of the hackers that attacked Brian Krebs, they enlisted over 1.5 million hacked cameras all over the world to become pawns in bringing his website down.
The camera’s became Zombie Robots all working simultaneously to inundate his blog with hundreds and thousands of HTML request every second.
But how the heck did they manage to assemble so many cameras so quickly to do so much damage?
Dumb Passwords and Cameras Were the Weakest Link
Fraudsters and hackers always look for the weakest link. In this case it was dumb passwords or “default passwords” that manufacturers installed in the security software of cameras.
Now most cameras are not continuously connected to the internet but some are like security cameras, IP cameras and baby monitors. These are often the targets the hackers choose.
And most consumers don’t think twice about changing the dumb username and password that comes loaded with the camera from the manufacturer. Those dummy passwords became the weakest link that the hackers exploited to take control of the camera’s and turn them into robots that would attack his site.
Here are some examples of camera brands and their dummy username and passwords;
- Canon– (UserName – Root, Password – camera)
- Panasonic– (UserName – Admin, Password – 12345)
- Sanyo -(UserName – admin, Password – admin)
- Toshiba– (UserName– root, Password – root)
- JVC– (UserName – Admin, Password – jvc)
You get the idea. So not only is this general knowledge among hackers that many cameras connected to the internet use these dummy passwords but there are lots of helpful links on the web that can give you these default username and password combinations. Like this one – IP Camera’s Default Password Directory.
To make matters worse though, some camera manufacturers security is so weak that hackers could commandeer the cameras by merely typing in random digits into the username and password fields.

Over the last couple of months the hackers have been proliferating the software and bringing on thousands and thousands of new devices everyday.
Krebs provided an additional list of camera manufacturers that have been used in the DDos attacks.
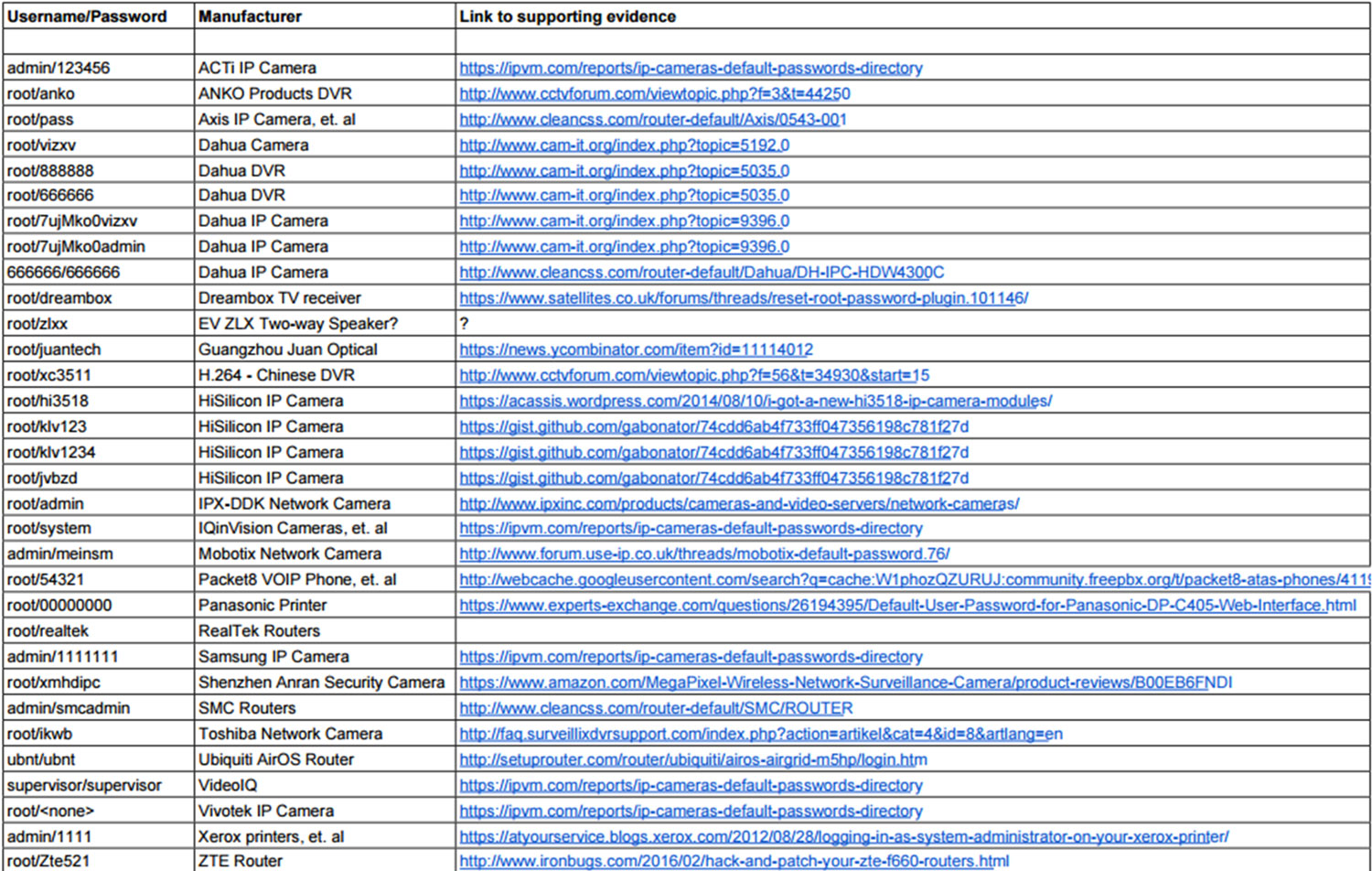
It’s hard to believe that camera’s are now on the frontlines of the war on cybercrime but they are, and it’s bad. Very bad.
The Source Code Was Released Which Means Chaos Will Continue
As if this all wasn’t bad enough, the hackers just released the source code to the DDoS software that brought down Krebs site. Using the code name “Anna Senpai” the hacker indicated that he was getting out of the business because he had made so much money and he was ready to let others use it in the same way.
Day by day, these same malicious hackers are assembling larger and larger armies of internet connected devices and cameras across the world. As they grow, so will the chaos that ensues.
What Should You Do?
There are 2 easy things you can do to attempt to decommission your devices from these “Robot Armies”.
- You can reboot your devices which can remove the code from memory and
- You can change your device password from the default dummy passwords provided in the factory settings.
Simply rebooting the device alone may not solve the problem because there is so much scanning by hackers for devices that they can be re-infected almost immediately after rebooting. You should do both to stop the security loophole from being exploited.
Thanks for reading. Please drop me a line if you have any comments or questions.



