The sophistication of emulators and fraud tactics on mobile is getting so advanced that fraudsters have figured out new ways to bypass banks’ fraud controls.
And that could spell big trouble for the coming years as banks scramble to update their mobile fraud strategies to respond to updated attacks on their highest growth channel.
IBM Trusteer investigators uncovered a massive fraud ring that reportedly used emulators to mimic consumers’ phones and was successful in stealing millions of dollars from online banks.
Banks are increasingly concerned with just these types of attacks since fraud originating from mobile devices has been on the increase for years.
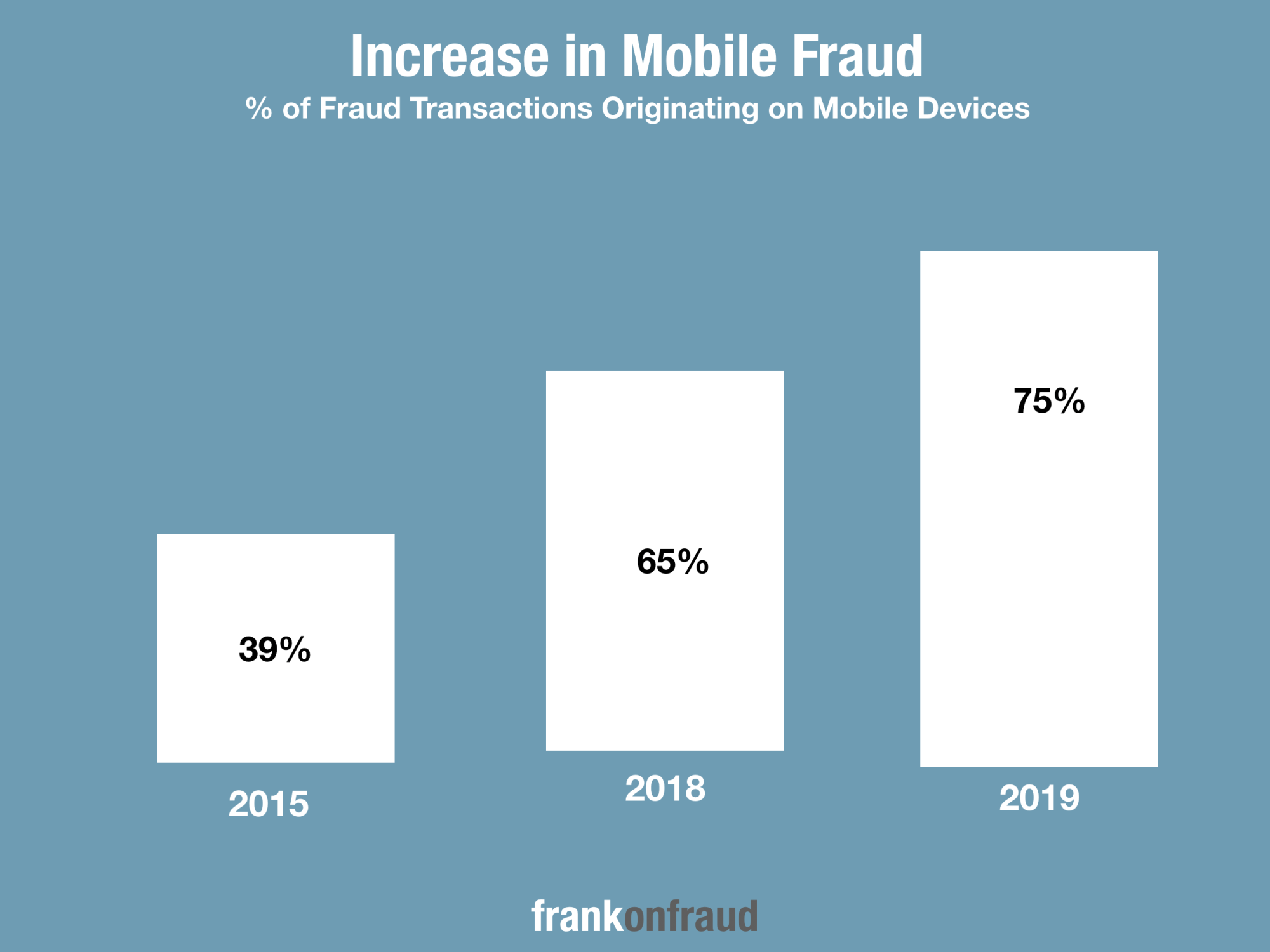
The scheme was designed to carefully circumvent fraud controls and monitoring that banks use to prevent mobile fraud such as device identification, negative files and SMS messaging.
Unlike Anything Investigators Have Ever Seen Before
The scale of the operation is “unlike anything seen before”. In one case, fraudsters used 20 emulators to mimic more than 16,000 phones belonging to customers whose mobile bank accounts had been compromised. In another case, a single emulator was able to spoof more than 8,100 devices.
The fraudsters entered usernames and passwords into banking apps running on the emulators and initiated fraudulent money orders that siphoned funds out of the compromised accounts.
To circumvent fraud detection banks use to block such attacks, the fraudsters used device identifiers corresponding to each compromised account holder and spoofed GPS locations the device was known to use.
The device IDs were likely obtained from the holders’ hacked devices, although in some cases, the fraudsters gave the appearance that they were customers who were accessing their accounts from new phones. The attackers were also able to bypass multi-factor authentication by accessing SMS messages.
The report originally appeared in ARS Technica and was based on a blog post by Trusteer employees Shachar Gritzman and Limor Kessem.
Emulators Were Used To Request Fraudulent Money Orders
Trusteer’s mobile security investigators laid out the foundation of the scheme that the fraudsters used which included the following components.
- Access to account holders’ usernames and passwords
- Access to device identifiers and data likely gathered via compromised mobile devices.
- Some ability to obtain SMS message contents.
- A customized automation environment tailored to targeted applications and the logical flow of events to approve transactions.
- A set of virtual mobile emulators, dozens in each case, to amplify the ability to spoof a larger number of devices and cycle through new ones rapidly and at scale.
- Customized network interception scripts that communicated with the targeted application’s API. These interceptions both submitted transactions and also monitored communications to ensure that the fraud was not being detected.
After gaining entry into the banking app, the fraudsters would drain the banking accounts by requesting cash transfers out of the account.
The Emulators Were Well Disguised and Well Tested by The Fraud Ring
In the report written by Shachar Gritzman, he details that “within the network mounted to emulate devices, each emulator was set up carefully to either appear exactly like an actual device from the repository the attackers accessed or as a randomized “new” device.
And to ensure that the emulation was successful, the attackers ran tests and viewed device parameters by using a variety of legitimate apps they downloaded from official stores.
By creating those as a training environment, they were able to test and fine-tune the scripts and the actions their tools took in different situations. Only after perfecting the flow did they target customer accounts through the actual mobile banking apps of the banks they attacked.
When They Successfully Got A Fraud Money Order Through, They Would Change The Device ID
The emulators were well disguised and avoided banks’ negative file checks by not getting too greedy or lazy.
Gritzman indicates that, “Each time the system used a device in a successful fraudulent transfer, it was ‘recycled’ and replaced by another, unused device. The same happened when a device was blocked by the financial institution. In most cases, the attackers used existing device identifiers. However, in some cases, they created a randomized device to appear as if a customer was using a new device to access their account.”
They Used Sophisticated Monitoring To Detect When Things Were Not Going As Planned
To keep the scheme going, the crooks used “hooking” techniques that “listened and intercepted the communication with targeted application servers during the fraud attempts. Logs from the fraudulent sessions were recorded and sent to the attackers’ remote server, alongside screen captures from the targeted application.”
They would monitor how the applications responded to their connection attempts, and if something was getting blocked, they could quickly change their tactics, or wipe away any evidence that they were there altogether.
This Is A Sophisticated Group of Hackers, Unlike Any Other
Trusteer’s investigators concluded that this scheme was likely perpetrated by very sophisticated hackers, and speculate it could be the work of hackers similar to Evil Corp, the Russian hacking group that has been linked to the Russian government.
They also note the growing trend of groups providing just this type of sophistication for a fee with Fraud for Hire Services.
Gritzman warns that Fraud For Hire services are underground venues that promises access to the same type of operation to anyone willing to pay for it, with or without the required skill. This lowers the entry bar for would-be criminals or those who plan to transition into the mobile fraud realm. It also means this at-scale automation scheme can be adapted to almost any financial institution in a variety of countries and territories and is likely to become a growing trend among cybercriminals.
Trusteer Stresses The Importance Of Educating Your Customers
IBM Trusteer stressed the importance of educating consumers on the risk of mobile fraud.
After concluding their research, they recommended the following to minimize their liklihood of mobile fraud;
- Avoid jailbreaking or rooting any of your devices.
- Ensure all system updates and app updates take place on time.
- Delete apps no longer in use.
- Obtain apps directly from official app stores.
- Ensure apps being downloaded are from a legitimate developer/company.
- Check your bank statements and report suspicious account activity promptly.
- Be aware of SMS notifications, Banks do not notify you of account issues via SMS text.
Mobile fraud is continuing to grow in size and sophistication. The time is now to take it seriously and develop an effective strategy and response.



